
Published May 30, 2023 | Threat Intelligence
This article is English version of “USBメモリを起点としたFlowCloudを用いた攻撃について” translated by Hisayo Enomoto, NTTSH SOC analyst.
This article is authored by our SOC analysts, Shogo Hayashi, Fumio Ozawa and Rintaro Koike.
Introduction
Over the past year, our SOC has observed attacks via USB flash drives by targeted attack groups such as Mustang Panda [1], KilllSomeOne [2], and TA410 [3]. Although these attacks are against Japanese organizations, many of them occur at overseas locations.
Particularly since early 2022, we have confirmed FlowCloud [4] infections in several organizations. FlowCloud is malware used by an attack group called TA410 and has been observed since around 2019. TA410 used to target US public institutions, but in recent years it has been classified into three subgroups [5] and is known to target a wide range of global organizations.
According to the ESET blog [5], one of the attacks in Japan was against a manufacturing company and exploited ProxyShell vulnerability. The attack was attributed to a subgroup called LookingFrog. However, the recently observed attacks use FlowCloud malware, which is considered a subgroup called FlowingFrog rather than LookingFrog. Since these attacks have been observed at multiple Japanese organizations and have been conducted against the same industry over several months, they are most likely targeting Japanese companies with some clear purpose.
In this article, we present recent FlowCloud observation status, attack chain, and malware samples.
Observation in Our SOC
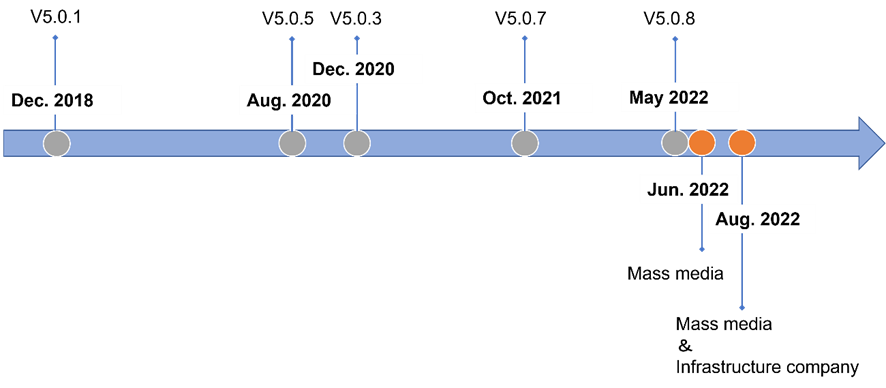
The following figure shows a creation date for each version of the FlowCloud installer our SOC collected, as well as durations of the attacks and targeted industries we observed.
Although creation dates of installers are tentative because they can be easily tampered with by attackers, we have confirmed that various versions of FlowCloud had been used over several years, and multiple attacks were conducted in a short period of time from June to August 2022
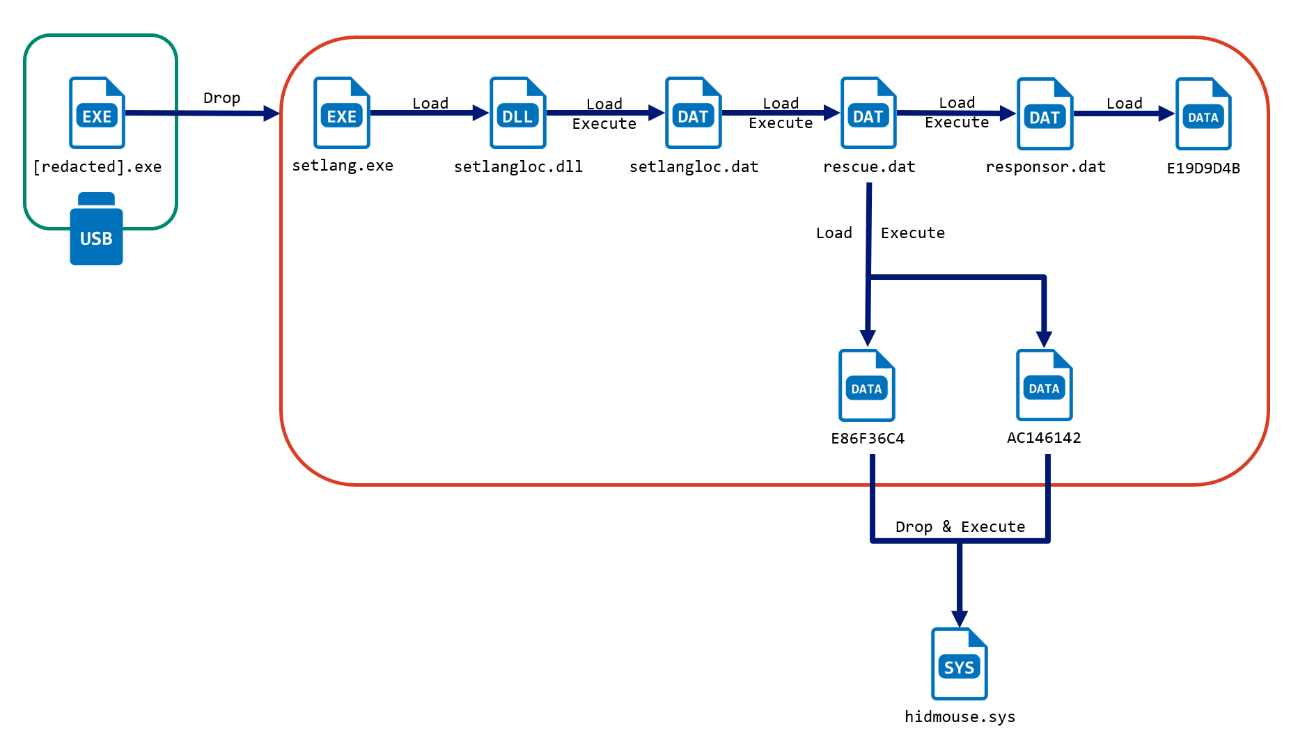
Attack Chain
The following is an attack chain of a FlowCloud v5.0.8 sample we have obtained. The behavior after running a FlowCloud installer is basically the same as in the previous report published by ESET [5], and nothing noteworthy. However, it is notable that while previous attacks began with an RTF file built with Royal Road RFT Weaponizer or a vulnerability exploit such as ProxyLogon or ProxyShell, this attack campaign originated from a USB flash drive.
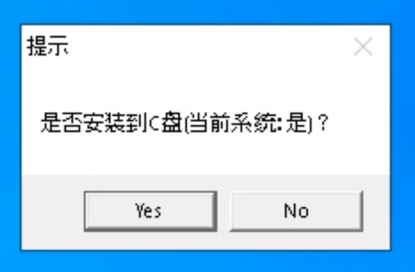
Running the EXE file on the USB flash drive deploys and executes FlowCloud. In the case of FlowCloud v5.0.7 or later, a message “是否安装到C盘(当前系统:是)?” (English Translation: Do you want to install on C drive (Current System: yes) ? ) will appear. We think this is because the EXE file is disguised as some kind of installer.
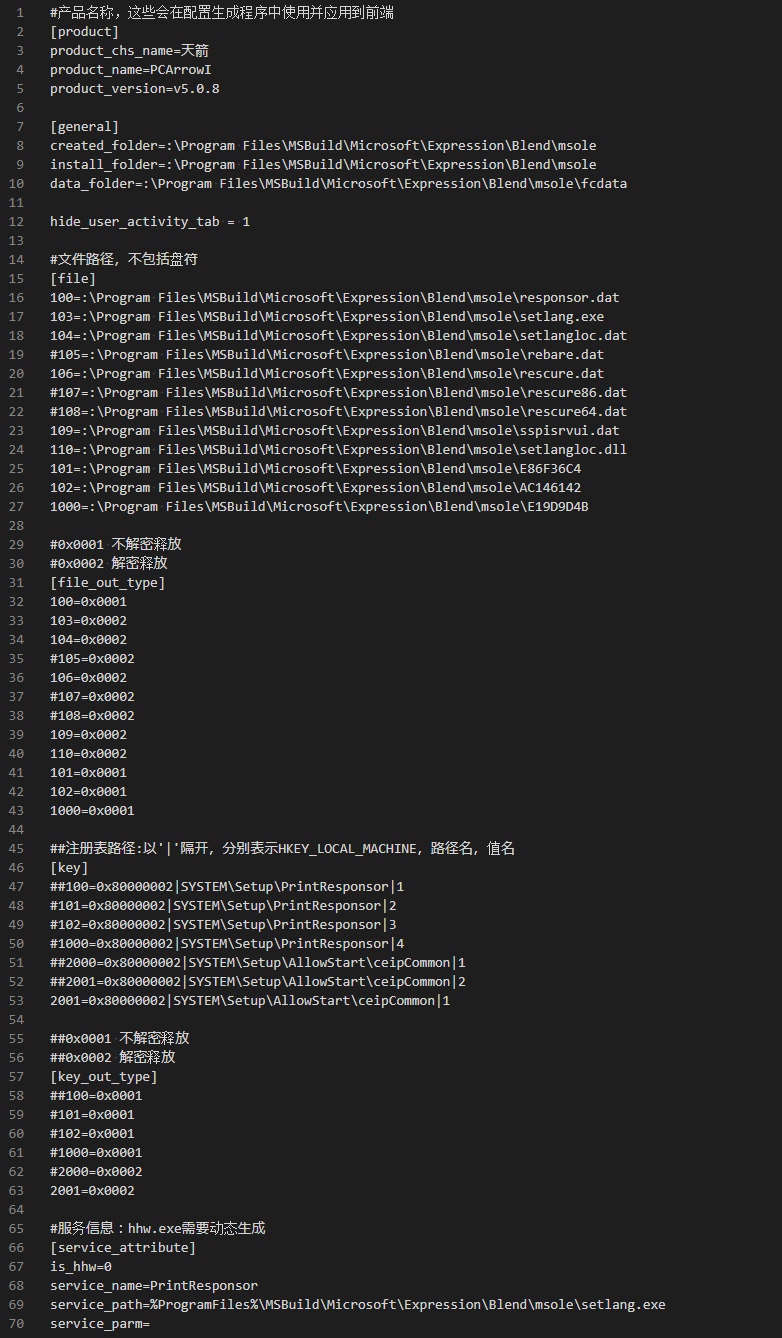
FlowCloud Implementation
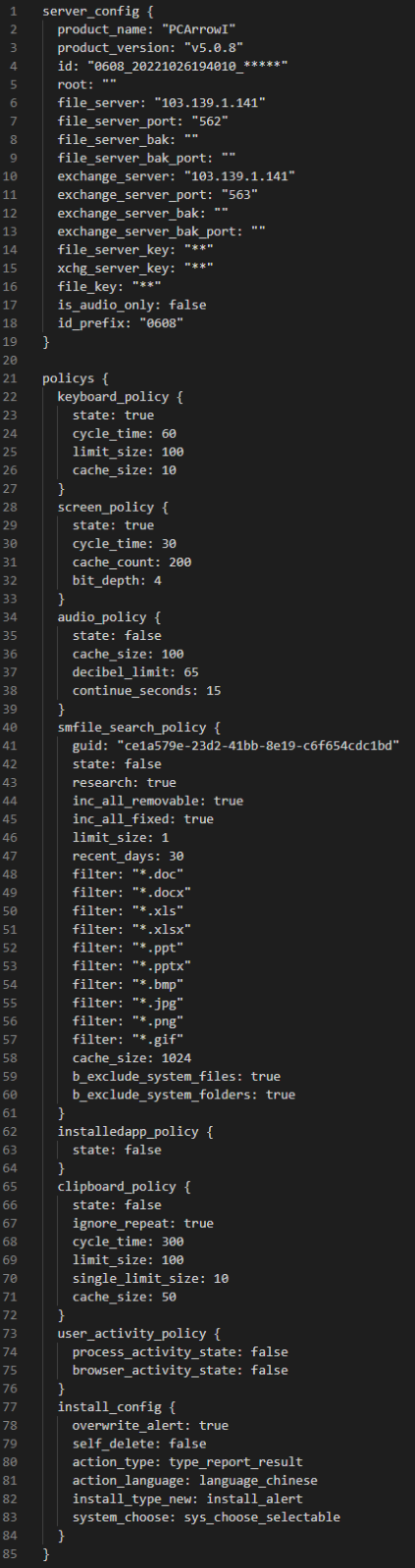
The FlowCloud v5.0.8 sample we obtained deploys a FlowCloud installation configuration in memory when the installer is executed, as shown below. This installation configuration defines embedded resources and file paths where they are located and contains explanatory comments in Simplified Chinese.
A backdoor module fcClinetDll.dll, which implements main backdoor features, is a DLL file obtained by decrypting responsor.dat and calls the startModule export function. Our sample implemented additional classes related to task management, such as fc_offline_task_manager, fc_net::msgOfflineTask and fc_net::msgOnlineTask, compared to v5.0.3 [5] analyzed by ESET. The backdoor module reads and decrypts the file E19D9D4B and then deploys the following Config in memory. The Config shows that this sample communicates on ports 562 and 563.
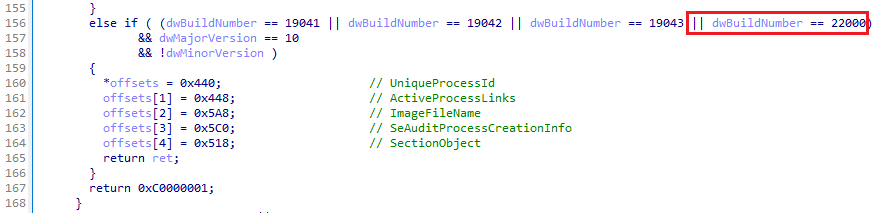
In addition, as ESET reports [5], a rootkit is executed by installing a driver prepared by an attacker. The rootkit implements a feature to hide processes by removing a targeted process entry from a process list of an undocumented EPROCESS structure. Since the internal structure of the EPROCESS structure may vary depending on the OS versions, different offset values are required for each OS build. We have confirmed that offset values of build number 22000 have been added to this driver, which means that it is compatible with Windows 11 Version 21H2.
Command and Control Server
Our analysis of FlowCloud v5.0.1 and its later versions confirmed that many samples have destination IP addresses directly listed in the malware Config. We investigated the WHOIS information on these IP addresses and found that most of them were located in China. Additionally, port numbers used for communication are not the commonly used ones such as TCP/80 or TCP/443, but various unusual port numbers such as TCP/562 or TCP/55555.
Judging from these characteristics, the method of infection via USB flash drive and Chinese message when the file is launched, it is possible that the target of these FlowCloud attacks is China, but our SOC has not yet had sufficient evidence.
Note that infection can be prevented by closing unnecessary or unused ports from internal to external network with a firewall.
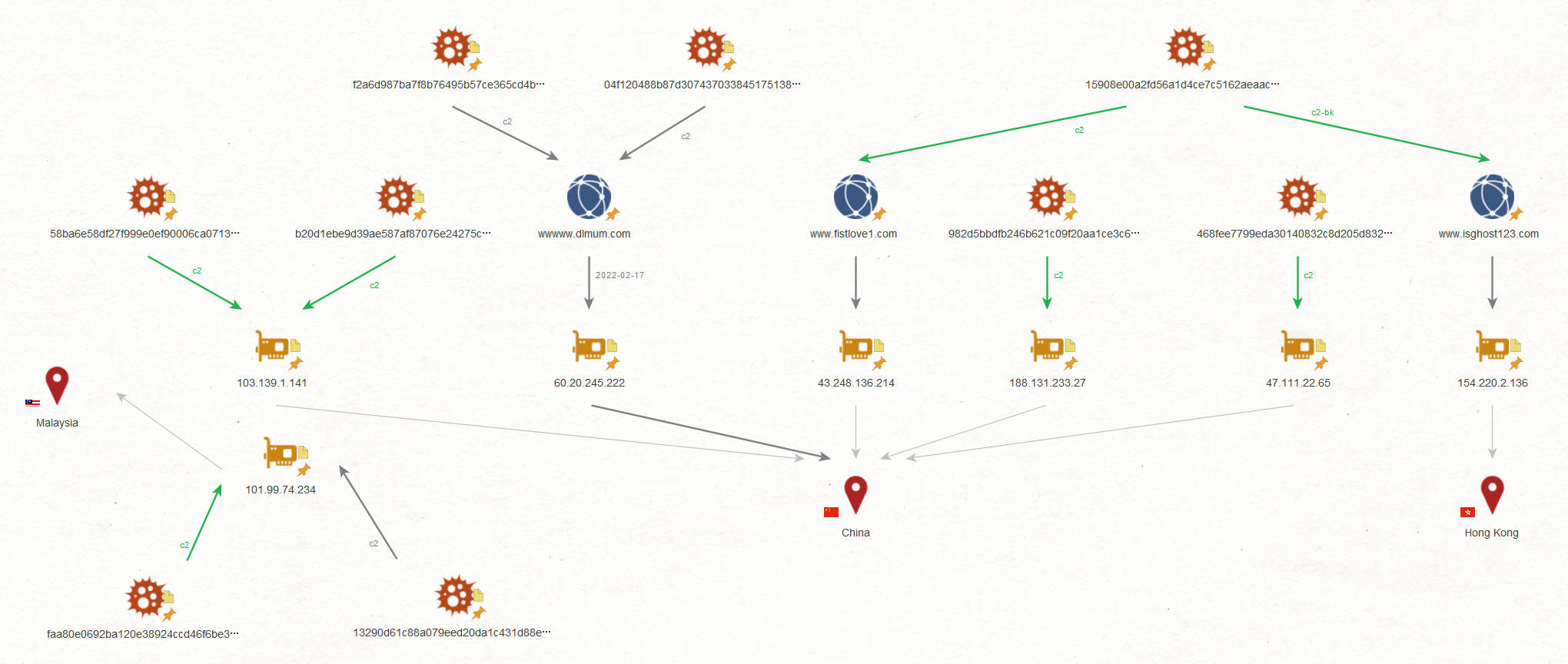
Relevant Samples
A FlowCloud v5.0.3 sample (04f120488b87d307437033845175138abb44795624819911195f71cf5132ed89) was posted to VirusTotal on February 17, 2022, and a sample (f2a6d987ba7f8b76495b57ce365cd4b89ecd5a81e5c80633914e97f1304aa947) using the same C&C server (wwwww.dlmum[.]com) was also posted at about the same time.
This FlowCloud v5.0.3 sample is very similar to the droppers described in previous Symantec and Positive Technologies reports [6][7] on an attack group called Webworm or SpacePirates. Webworm/SpacePirates is suspected to be related to TA428, and TA428 is also known to have shared attack tools with TA410 in the past [8]. This indicates some connection between these two attack groups.
Detection and Analysis
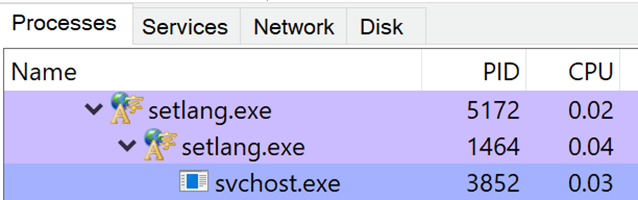
The execution behavior of FlowCloud installer is very similar to that of a legitimate software installer. Therefore, even if EDR solutions detect the behavior with some signatures, it is difficult to determine that it is a malware infection. However, take a look at the entire attack chain from the execution of the FlowCloud installer to the infection behavior by the RAT. We have confirmed that the installer initiates itself as a child process, launches svchost.exe as a grandchild process, injects the FlowCloud RAT into svchost.exe, and accesses the C&C server.
Therefore, EDR solutions can detect the behavior, and determine malware infection from them when analyzing logs. Even if the version of FlowCloud changes, the file names and paths do not change much, so the information can be utilized to further improve the detection accuracy.
Conclusion
In this article, we provided attack cases of FlowCloud targeting Japanese organizations. It is worth noting that the attack originates from a USB flash drive. Even in recent years, there have been several targeted attack groups using USB flash drives to attack Japanese companies. Even if domestic organizations have established rules for the use of USB flash drives, these rules might not be followed at overseas offices. It is necessary to understand the actual conditions, review your organization's policies and implement measures to protect your organization from these attacks.
References
[1] Avast, "Hitching a ride with Mustang Panda", https://decoded.avast.io/threatintel/apt-treasure-trove-avast-suspects-chinese-apt-group-mustang-panda-is-collecting-data-from-burmese-government-agencies-and-opposition-groups/
[2] Sophos, "A new APT uses DLL side-loads to “KilllSomeOne”", https://news.sophos.com/en-us/2020/11/04/a-new-apt-uses-dll-side-loads-to-killlsomeone/
[3] Proofpoint, "LookBack Malware Targets the United States Utilities Sector with Phishing Attacks Impersonating Engineering Licensing Boards", https://www.proofpoint.com/us/threat-insight/post/lookback-malware-targets-united-states-utilities-sector-phishing-attacks
[4] Proofpoint, "TA410: The Group Behind LookBack Attacks Against U.S. Utilities Sector Returns with New Malware", https://www.proofpoint.com/us/blog/threat-insight/ta410-group-behind-lookback-attacks-against-us-utilities-sector-returns-new
[5] ESET, "A lookback under the TA410 umbrella: Its cyberespionage TTPs and activity", https://www.welivesecurity.com/2022/04/27/lookback-ta410-umbrella-cyberespionage-ttps-activity/
[6] Symantec, "Webworm: Espionage Attackers Testing and Using Older Modified RATs", https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/webworm-espionage-rats
[7] Positive Technologies, "Space Pirates: analyzing the tools and connections of a new hacker group", https://www.ptsecurity.com/ww-en/analytics/pt-esc-threat-intelligence/space-pirates-tools-and-connections/
[8] nao_sec, "Royal Road! Re:Dive", https://nao-sec.org/2021/01/royal-road-redive.html
IOCs
Version | Destination IPs/Domains | SHA256 |
v5.0.8 | 103[.]139.1.141 | 58ba6e58df27f999e0ef90006ca071356abc786d46390a4a059a5855037c3d39 |
v5.0.8 | www.fistlove1[.]com | 15908e00a2fd56a1d4ce7c5162aeaacbadf16f1f038a6b292e9ccee9b7553eb5 |
v5.0.7 | 103[.]139.1.141 | b20d1ebe9d39ae587af87076e24275cfc47de4cb4b6860607e25f61847a216d7 |
v5.0.5 | 47[.]111.22.65 | 468fee7799eda30140832c8d205d832e40cc98e09ee0c7b4d62e398c20162bae |
v5.0.3 | wwwww.dlmum[.]com | 04f120488b87d307437033845175138abb44795624819911195f71cf5132ed89 |
v5.0.1 | 101[.]99.74.234 | faa80e0692ba120e38924ccd46f6be3c25b8edf7cddaa8960fe9ea632dc4a045 |
v5.0.1 | 188[.]131.233.27 | 982d5bbdfb246b621c09f20aa1ce3c6649708a76600896981ba17c6996a34402 |
v5.0.1 | 101[.]99.74.234 | 13290d61c88a079eed20da1c431d88e71b540844fec2af6942a2763962f8055a |


