
Published November 18, 2022 | Japanese
こんにちは、羽田です。11月3日の AVTokyo 2022 Day2 にて、Power Automate C2 というタイトルで発表しました。Power Automate は Microsoft 365 上で多様なサービスと連携して反復的なタスクを自動化するための強力なプラットフォームで、日常業務を簡略化するための様々なコネクタが用意されており、ノーコードでフローを作成できることから多くの利用者がいます。一方で、VECTRA 社のレポート のように、攻撃者に悪用されるケースも報告されています。この Power Automate のコネクタを眺めていて攻撃者に悪用されそうなシナリオを考えたので、今回の発表ではそのコンセプトと簡単なデモを紹介しました。
ちなみに、当日は現地参加が叶わなかったため動画での発表となってしまいました。現地の雰囲気を楽しむことができず残念でしたが、来年こそはオンサイトで発表できるように新たなネタを探したいと思います。

Power Automate の制約
攻撃者がある被害者ユーザーのアカウントで Power Automate にログインできる状況を想定します。この時、攻撃者は Power Automate で新着メールや共有ファイルなどを外部に送信するフローを作成することができます。このフローの実行ログは 28日間残りますが、フロー自体を削除するとログも即座に削除されます。例えば、攻撃者が外部に送信した情報の詳細を知られたくない場合、ユーザーに気づかれる前にフローを削除する必要があります。
以下の図は、フローの 28日分の実行結果と、その詳細ログの例です。
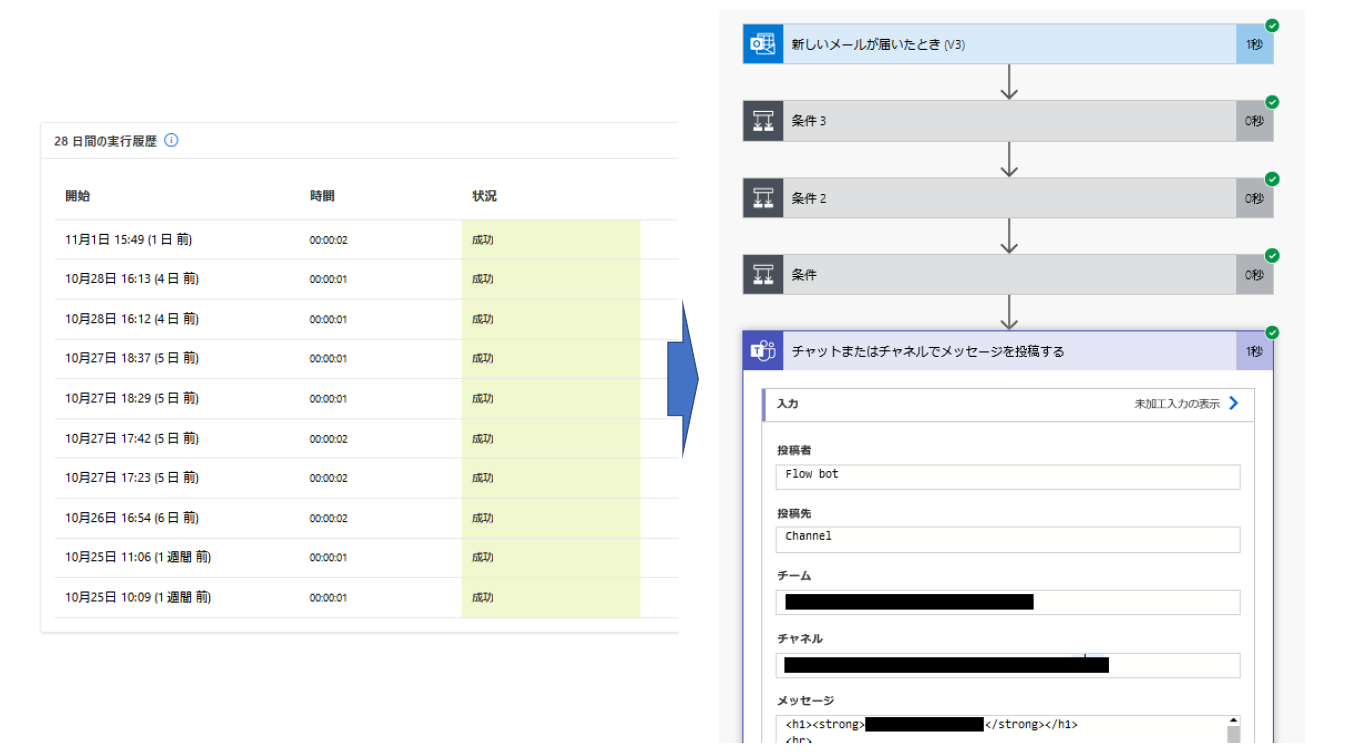
ここで、ユーザーは自分自身が侵害されたことを知らないとして、パスワード変更ポリシーの要請などの理由でたまたまパスワードを変更した場合を考えます。攻撃者は Power Automate にログインすることができなくなるため、このフローを削除したり、新たなフローを作成することはこれ以上できません。
Power Automate C2
そこで、Power Automate が提供する Power Automate Management というコネクタを利用することで、この制約を回避することを考えました。Power Automate Management は Power Automate のフローを管理するためのコネクタで、フローの作成や削除などが可能です。フローは JSON 形式で定義します。
Power Automate Management に対してリモートから JSON を送信して新しいフローを作成し、処理が完了したら削除する、ということを逐次的に繰り返すことで、攻撃者がペイロードに指定した任意のフローを指示して実行しながら、実行の痕跡を削除するという処理が可能となります。まさに Power Automate 上でフローが C2 マルウェアのように振る舞うので、これを Power Automate C2 と呼ぶことにしました。
攻撃シナリオ
あらためて攻撃シナリオを整理します。
- 攻撃者はユーザーを侵害して Power Automate へのアクセス権を入手し、悪意あるフローを作成する。
- 侵害されたことを知らないユーザーが、たまたまパスワードを変更する。
- 攻撃者は C2 経由で Power Automate へのアクセスを継続し、任意のフローを作成・実行する。
- 攻撃者は目的を達成したらフローとともに痕跡を削除する。
実装
今回は C2 サーバーとして Dropbox を使用しました。外部とデータの送受信ができれば何でも良いのですが、HTTP 接続を行う「HTTP アクション」コネクタはプレミアムライセンスが必要であり、使用できるかどうかは侵害されたユーザーの環境に依存するため、汎用的なコネクタを用いました。
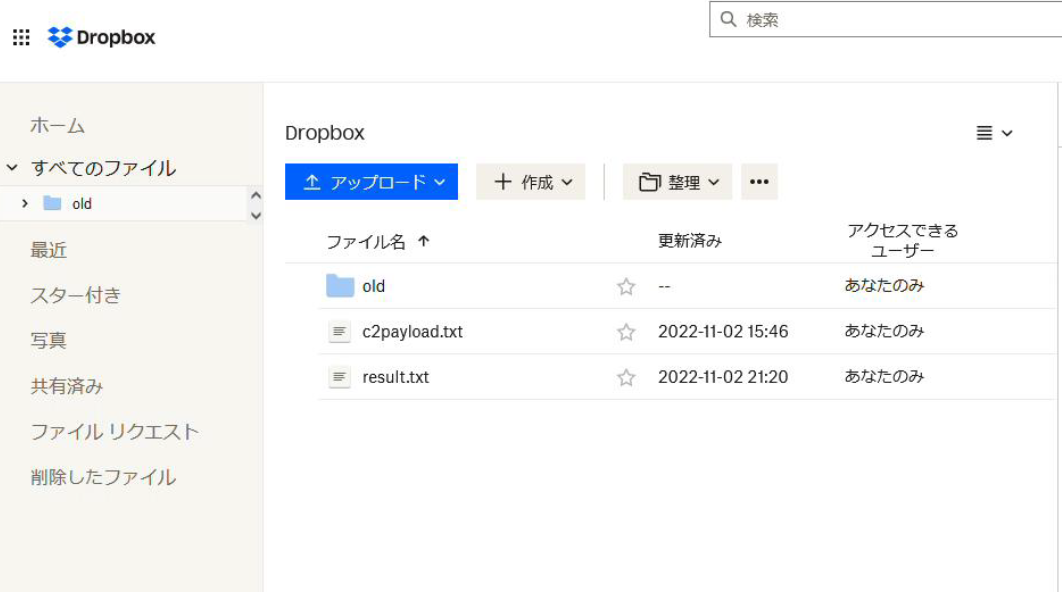
攻撃者の Dropbox アカウントには、以下のように c2payload.txt と result.txt が格納されています。c2payload.txt はフロー情報を定義した JSON ファイルです。result.txt は実行結果を受け取るためのファイルで、最初は空となっています。
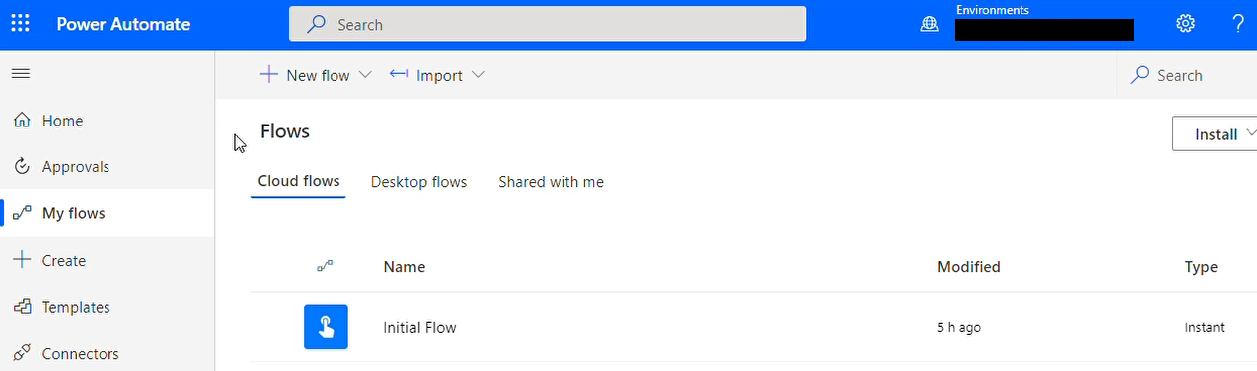
攻撃者は Power Automate にアクセスし、初期フローを作成します。初期フローは手動で作成するか、あらかじめパッケージ化しておいた zip ファイルをインポートすることで作成できます。
初期フローは以下のように、C2 サーバーから JSON(c2payload.txt)をダウンロードして、Power Automate Management でフローを作成し、自分自身を削除するというシンプルな構成となっています。
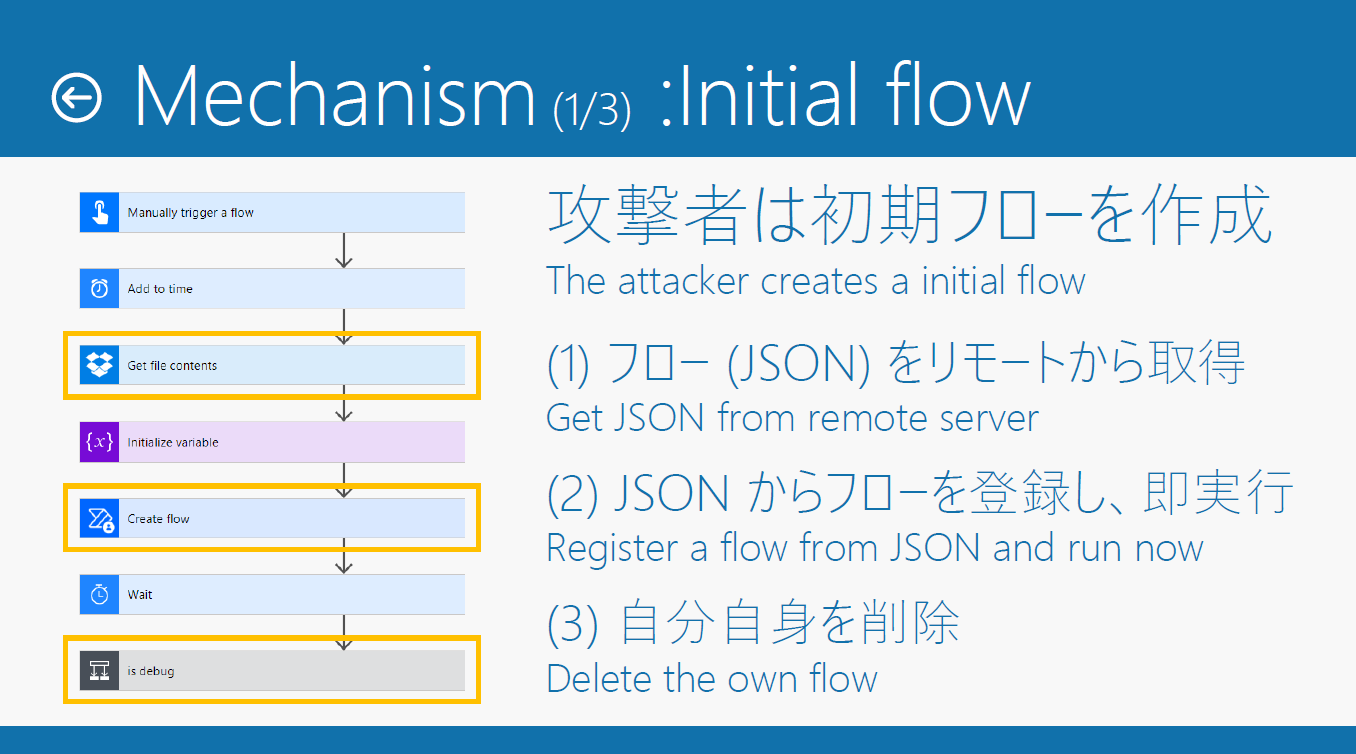
c2payload.txt で生成されたフローは以下のようになっています。左側は攻撃者が用意したペイロードとして任意のフローが構成されています(この図の例では Teams からコメントを抽出して Dropbox にアップロードしています)。右側は初期フローと同様の内容になっており、次のペイロードを呼び込みます。今回は 1分ごとにコマンドを取りにいくように wait で待機しています。
フローの一覧を表示すると、以下のように初期フローの他に新しく生成されたフローが 2つ確認できます。連鎖的にフローが生成され、古いものから削除されます。(本来であれば初期フローも削除されますが、今回はデバッグのため残しています)
生成されたフローの実行ログを確認すると、Power Automate Management の実行結果として次のフロー情報が JSON として記録されています。これを調査すると攻撃者が用意したペイロードが判明しますが、1分後のフロー削除とともにこの実行記録も削除されます。
攻撃者は目的を達成した後、最後に自分自身のフローを削除するだけのペイロードを送り込みます。これにより、最終的にフローが実行されたこと自体をユーザーから隠ぺいすることができます。
対策
発表時点ではフローをこまめにチェックする、Power Automate の侵害から守る、といった対策しか思いつかなかったのですが、@defenceability 氏から DLP ポリシーで Power Automate Management を利用禁止にする緩和策 が提案されました(大変感謝です)。これは Power Automate Management を使用しない場合、有効な対策になると考えます。
補足
Power Automate の仕様上、パスワード変更を行ってもすでに認証済みのコネクタは有効のままとなります。SSO としての特性、大量のフローやコネクタを使用しているユーザーに対する利便性、失敗時の業務影響などを考えると、この仕様を変更するのは難しいのではと考えています。
攻撃者の操作がクラウドで完結することを目標としたため、端末側で実行する Desktop Flow は今回は利用していません。圧縮や暗号化などの機能は Desktop Flow として用意されているため、使用しませんでした。
今回はコンセプトの紹介ということで、C2 サーバーの作りこみなどは行わず、c2payload.txt の差し替えや result.txt の引き上げなどは手動で行いましたが、自動化することも可能です。
おわりに
本発表では、C2 サーバーからフローを受け取って実行する Power Automate C2 を紹介しました。


